As technology forges ahead, redefines, and reshapes everything, it has also transformed workspaces. This effect has become even more prominent with the outbreak of Covid-19 in 2020. Nowadays, we are faced with new ways and more flexible workspaces. A digital workspace is a virtual environment that allows employees to access all the tools, applications, and data they need to perform their jobs from any device and location. To put it simply, a digital workspace is a centralized platform that eliminates the need for multiple logins and provides a consistent user experience across any device. This approach has many benefits not only for the employees themselves but also for IT admins. With today’s digital management capabilities, IT admins can troubleshoot devices from anywhere. They can also control access to corporate resources, enforce security policies, and monitor user activity from a single dashboard.
These benefits are not just limited to IT admins, as digital workspaces also enhance productivity by enabling employees to work from anywhere. Moreover, they can collaborate with team members and access the information they need in real time much more easily. Digital workspaces can reduce stress associated with commuting, office politics, and other workplace challenges, especially for the remote and hybrid workforce. By providing a secure and flexible work environment, digital workspaces can heavily improve employee satisfaction and retention.
Key Components of a Digital Workspace
A digital workspace has many components. Since there are many solutions to cover, we will focus on the main ones.
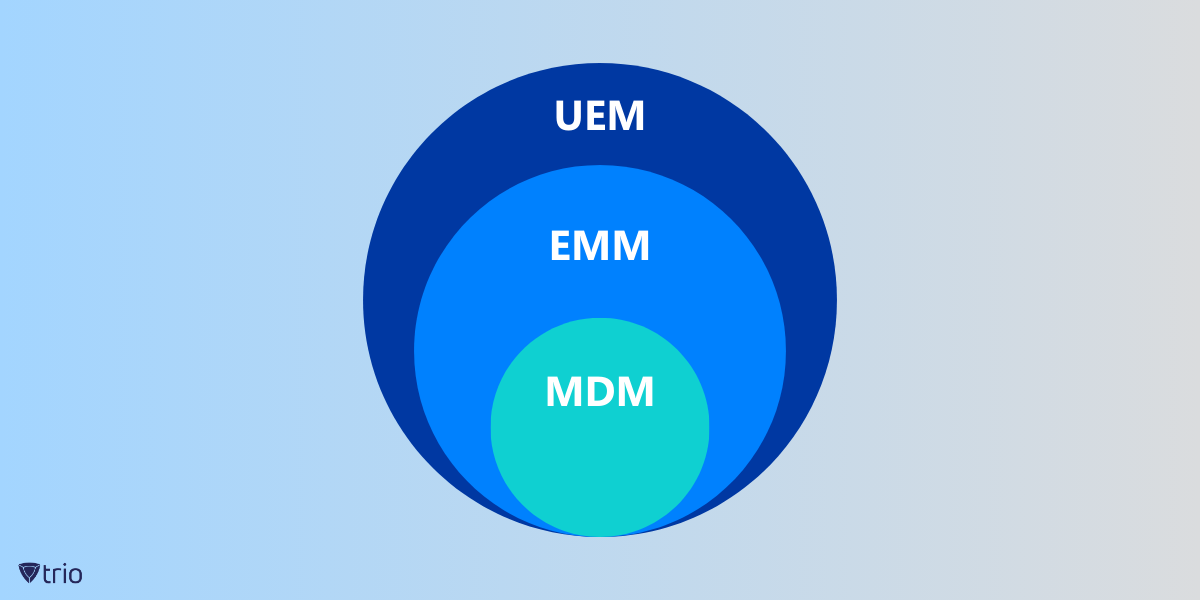
Unified Endpoint Management (UEM)
UEM is an all-encompassing, centralized approach to endpoint management. To make it simpler, a UEM solution monitors and secures all types of endpoints, including desktops, laptops, mobile devices, and IoT devices, from a single console. A UEM solution helps IT admins manage device configurations, software updates, security policies, and user profiles across all endpoints. UEM solutions also support remote work and bring-your-own-device (BYOD) policies by providing secure access to corporate resources from any device.
Enterprise Mobility Management (EMM)
Compared to UEM, which has a broader scope when it comes to endpoint management, EMM takes a more moderate approach. EMM predominantly encompasses the management of mobile devices, applications, content, and data. It provides organizations with a comprehensive set of tools and policies to control, deploy, and secure mobile devices and associated resources. In other words, EMM historically has had a more focused approach to mobile devices and apps. While some EMM solutions have expanded functionality to include aspects of endpoint management, they may lack the comprehensive coverage and integration capabilities offered by UEM.
Mobile Device Management (MDM)
Lastly, MDM solutions primarily focus on managing and securing mobile devices. It provides organizations with centralized control and configuration capabilities for mobile devices, including smartphones, tablets, laptops, and rugged devices. Its key functionality includes device enrollment, policy enforcement, app distribution, remote management, and security measures like passcode enforcement and device encryption. MDM is typically device-centric and works well in environments with a predominantly mobile workforce.
Identity and Access Management (IAM)
IAM is a framework designed for organizations to manage and control user identities and their access levels. It mainly covers processes and policies to ensure the right individuals have the appropriate access to the right resources at the right time. IAM solutions enhance security by diminishing the risk of unauthorized access. It also helps ensure compliance with the latest regulations. Moreover, it streamlines user management processes and productivity by providing seamless access to resources and simplifying password management.
Assessing Readiness for a Digital Workspace
But how can you know if your organization is ready for this drastic change? Assessing readiness for a digital workspace involves evaluating the current IT infrastructure, identifying potential challenges, and setting up the necessary policies. It’s crucial to ensure that the existing technologies implemented in your organization can support the digital workspace. If not, upgrades or changes must be made. Potential challenges, such as security concerns or lack of employee training, should be addressed by setting the right policies and guidelines. These policies include both the employees and all endpoints to ensure that employees understand how to use the resources effectively and securely. It’s important to note that all these concerns can be easily addressed by implementing the right MDM solution.
Designing a Digital Workspace Strategy
After making sure that the organization in mind is ready for the changes that are about to happen, the very first step is to consider the goals and, more importantly, the scope of the digital workspace implementation. This might seem like an insignificant step, yet it’s necessary for a successful rollout. This also involves identifying the specific tools and applications that are needed, as well as the expected outcomes and possible benefits. The next step includes determining the roles and responsibilities of IT admins, which is vital for keeping everything up and running. Apart from that, it’s only feasible to establish clear communication. This is to ensure that employees can easily access support and assistance when needed. For the final step, setting up security measures for remote access is essential to protect sensitive data and prevent unauthorized access. This step can be regarded as the most important step as it keeps organizations secure and protected from data breaches. This may involve implementing multi-factor authentication, encryption, and other security measures to ensure that only authorized users can access the digital workspace.
Implementing a Digital Workspace
After designing the digital workspace that you have in mind, the action begins. It’s essential to provide necessary training and support for IT admins and employees alike to guarantee successful implementation. IT admins, as it’s apparent, will need to be trained in how to manage and maintain the digital workspace. Employees, on the other hand, will need to be trained in how to use the tools and applications included in the workspace. Additionally, ongoing support is essential to ensure that any issues or concerns are addressed on time. It’s necessary to deploy solutions for managing remote devices and data access, as this will allow secure access to company resources from anywhere. Finally, testing and refining the digital workspace strategies is crucial to ensure that they are meeting the needs of employees and providing the expected outcomes and benefits. Regular evaluations and adjustments are also necessary to optimize the digital workspace for maximum efficiency and productivity.
Monitoring and Improving the Digital Workspace
After the successful implementation of your digital workspace solution, it’s essential to monitor and improve it regularly. This step is crucial to ensure that everything remains effective and efficient. Additionally, collecting feedback from IT admins and employees can provide valuable insights into areas that need improvement or additional support. Analyzing performance metrics, such as user adoption rates and productivity levels, can also help identify areas for improvement. As technology continues to evolve, new tools and applications may become available that can enhance the digital workspace experience. Therefore, it’s important to maintain patch management to ensure that your workspace remains relevant and effective as time moves forward.
See Trio in Action: Get Your Free Trial Now!
Trio Suitable for Any Digital Workspace
Trio offers a comprehensive Unified Endpoint Management (UEM) solution that enables organizations to create an optimal digital workspace. With Trio, IT administrators can easily configure policy profiles and apply desired restrictions across all types of devices. Trio also integrates seamlessly with other systems, simplifying user identity management and making app distribution and software management more efficient throughout the enterprise. Trio’s UEM solution ensures consistent security measures across all endpoints, reducing the risk of data breaches and enhancing compliance. By providing a centralized approach to endpoint management, Trio helps achieve productivity and save costs while delivering a seamless user experience.
A digital workspace is an essential component of modern businesses. This further helps enable organizations to achieve greater productivity and cost savings while delivering a seamless user experience. However, before implementing a digital workspace, it’s important to assess readiness, design a strategy, implement the solution, and monitor and improve it regularly. By following these steps and using the right tools, like Trio, organizations can create an optimal digital workspace that enhances productivity, security, and compliance. As technology continues to evolve, it’s important to stay updated and adapt to new trends and tools to ensure that the digital workspace remains effective and relevant. Trio is a MDM solution with a free trial available for you to check out today.




