In the fast-paced world of IT, the unexpected can disrupt operations. IT administrators play a pivotal role in fortifying organizations against potential disasters. This guide provides practical steps for administrators to build resilient infrastructures, understand the types of disasters, and implement effective disaster recovery plans. From minimizing downtime to protecting critical data, these strategies for disaster recovery ensure business continuity in today’s ever-evolving technological landscape. Additionally, IT Risk Management is essential for identifying, assessing, and mitigating potential risks that could threaten the security and stability of IT systems. By integrating IT Risk Management practices into disaster recovery plans, organizations can proactively address vulnerabilities and safeguard against unforeseen threats, further enhancing their resilience in the face of adversity.
What Is Considered a Disaster?
In the realm of information technology and disaster recovery planning, a disaster is broadly defined as any event or circumstance that significantly disrupts normal business operations and jeopardizes the integrity, availability, and confidentiality of critical data and systems. Disasters can take various forms, ranging from natural disasters to human-induced incidents, and they can have severe consequences if not adequately addressed. Here are some key categories of events that are considered disasters in the context of IT:
-
Natural Disasters
Natural disasters such as earthquakes, floods, hurricanes, tornadoes, and wildfires can cause physical damage to data centers, servers, and other IT infrastructure. The destructive force of these events can lead to power outages, equipment failures, and the loss of critical data.
-
Cyberattacks
Cybersecurity threats, including malware, ransomware, and hacking incidents, are a growing concern for IT administrators. These attacks can compromise the confidentiality, integrity, and availability of data, disrupt services, and lead to data breaches. Recovering from a cyberattack involves not only restoring systems but also addressing potential data exposure and reputational damage which can be done by disaster recovery planning.
-
Hardware Failures
Malfunctions or failures of hardware components such as servers, storage devices, or networking equipment can result in downtime and data loss. Redundancy and failover systems are essential components of disaster recovery strategies to mitigate the impact of hardware failures.
-
Human Errors
Mistakes made by employees or administrators, whether accidental or intentional, can lead to data loss or system outages. This may include accidental deletion of critical data, misconfigurations, or inadvertent exposure of sensitive information. Training and strict access controls are crucial for minimizing the risk of human-induced disasters.
-
Power Outages
Power disruptions, whether due to natural causes or infrastructure issues, can result in sudden shutdowns of IT systems. Unplanned power outages can lead to data corruption and hardware damage. Implementing uninterruptible power supply (UPS) systems and backup generators is vital to maintain continuous operations during power failures.
-
Supply Chain Disruptions
Events that impact the supply chain, such as geopolitical issues, pandemics, or economic crises, can have cascading effects on IT infrastructure. For example, disruptions in the supply chain for hardware components or cloud services can impact the availability of critical resources.
-
Environmental Factors
Factors like temperature extremes, humidity fluctuations, and environmental contaminants can impact the physical conditions of data centers. Proper environmental controls and monitoring are essential to prevent equipment overheating and reduce the risk of hardware failures.
-
Software Failures
Software bugs, glitches, or failures can result in system crashes and data corruption. Regular software updates, testing, and quality assurance practices help mitigate the risk of software-related disasters like cloud disaster recovery.
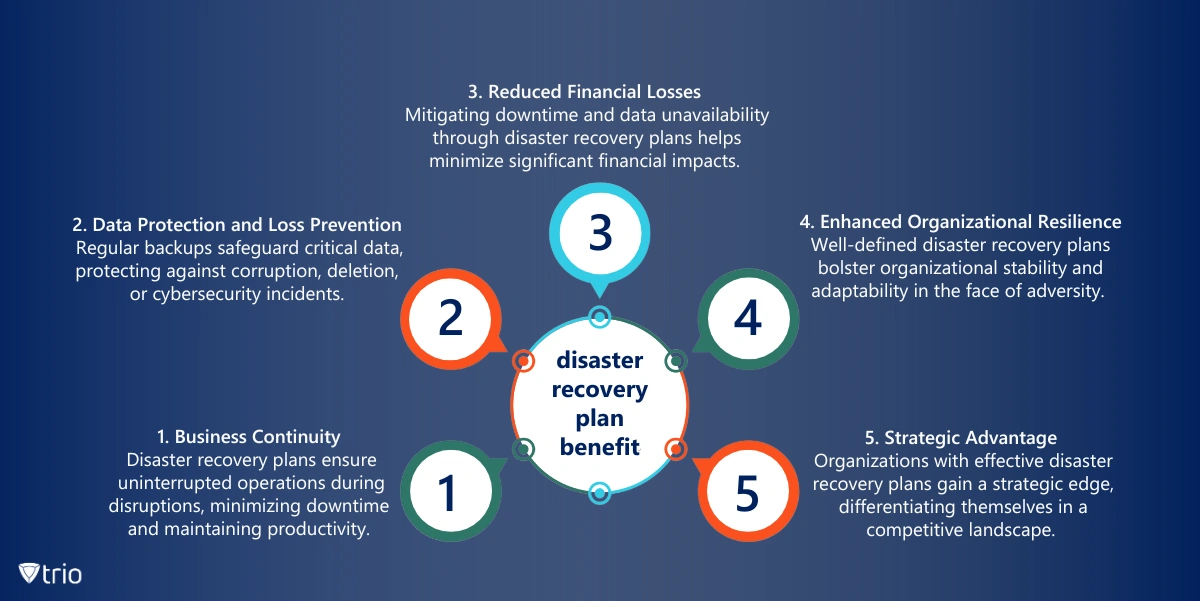
Benefits of Disaster Recovery
Beyond merely mitigating risks and vulnerability management, a well-executed disaster recovery plan offers numerous benefits. These include:
- Improved operational efficiency
- Reduced financial losses
- Enhanced organizational resilience
Additionally, businesses with robust disaster recovery mechanisms are better positioned to adapt to evolving technological landscapes and emerging threats.
Planning a Disaster Recovery Strategy
Developing effective disaster recovery strategies is a crucial responsibility for IT administrators, as it ensures business continuity and minimizes the impact of unforeseen disruptions. Here’s a step-by-step guide on how IT administrators should approach the creation of disaster recovery strategies:
-
Conduct a Comprehensive Risk Assessment
Before formulating a disaster recovery plan, IT administrators need to conduct a thorough risk assessment. Identify potential risks and threats that could impact IT infrastructure, including natural disasters, cyberattacks, hardware failures, and human errors. Understanding these risks is essential for prioritizing efforts and resources.
-
Perform a Business Impact Analysis
Once risks are identified, conduct a business impact analysis. Evaluate the potential consequences of downtime on financial, operational, and reputational aspects of the organization. This analysis helps in prioritizing critical systems and data that require immediate attention during a recovery process.
-
Define Objectives and Priorities
Clearly define the objectives of the disaster recovery plan. Determine recovery time objectives (RTOs) and recovery point objectives (RPOs) for different systems and applications. This involves setting specific targets for how quickly systems should be restored and how much data loss is acceptable in case of a disruption.
-
Select Appropriate Disaster Recovery Solutions
Choose the right mix of disaster recovery solutions based on the organization’s needs. This may include on-site, off-site, or cloud-based recovery plans. Each option has its advantages and drawbacks, so IT administrators should tailor the strategy to the organization’s specific requirements and budget constraints.
-
Implement Redundancy and Failover Systems
To ensure the continuous availability of critical systems, IT administrators should implement redundancy and failover mechanisms. This involves duplicating hardware, software, or entire systems, allowing for seamless transitions in the event of a failure. Redundancy minimizes downtime and contributes to a more resilient infrastructure.
-
Establish Data Backup Protocols
Develop a robust data backup plan, encompassing regular and automated backups of critical data. Store backups in secure offsite locations to protect against physical damage to on-premises servers. Regularly test the backups to ensure they can be quickly and effectively restored when needed.

-
Create a Communication Plan
Communication is key during a disaster. Develop a comprehensive communication plan that outlines how stakeholders will be informed in case of an incident. This includes internal teams, external partners, and customers. Clearly define roles and responsibilities to ensure a coordinated response.
-
Train and Educate Staff
Ensure that the IT team and relevant staff members are well-trained in the disaster recovery plan. Conduct regular drills and simulations to familiarize them with the procedures and identify any potential weaknesses in the plan. This proactive approach enhances the team’s preparedness and response capabilities.
-
Regularly Review and Update the Plan
Disaster recovery strategies should not be static documents. IT administrators must regularly review and update the plan to reflect changes in technology, business processes, and potential risks. This iterative process ensures that the plan remains effective and aligned with the organization’s evolving needs.
-
Document and Document Again
Comprehensive documentation is crucial. Ensure that all aspects of the disaster recovery plan, including procedures, configurations, and contact information, are well-documented. This documentation serves as a reference during crises and aids in the smooth execution of recovery efforts.
Conclusion
In a dynamic digital landscape, IT administrators bear the responsibility of fortifying their organizations against a spectrum of potential disasters. Using an MDM solution like Trio can go a long way in case there is ever a disaster, though it has many other benefits as well. Recognizing the broad scope of threats, understanding the importance of disaster recovery, and implementing a strategic plan are critical steps toward building a resilient infrastructure. By embracing these best practices, IT admins can ensure the continuity of business operations and position their organizations for sustained success in an ever-changing technological environment. Get Trio today as an MDM solution to complement your disaster recovery plan.
Get Ahead of the Curve
Every organization today needs a solution to automate time-consuming tasks and strengthen security.
Without the right tools, manual processes drain resources and leave gaps in protection. Trio MDM is designed to solve this problem, automating key tasks, boosting security, and ensuring compliance with ease.
Don't let inefficiencies hold you back. Learn how Trio MDM can revolutionize your IT operations or request a free trial today!