In the ever-evolving landscape of information technology, establishing a robust IT compliance policy is not merely a box to be checked but a strategic imperative for organizations seeking to thrive in a digital age fraught with risks. Types of compliance, such as regulatory compliance, data privacy compliance, and industry-specific compliance standards, play a crucial role in ensuring that organizations adhere to legal and regulatory requirements, safeguard sensitive information, and maintain the trust and confidence of customers and stakeholders.
Beyond the conventional steps in crafting compliance policies, this blog explores advanced best practices that transcend the routine, aiming to fortify the organizational framework against a myriad of challenges. From cultivating a compliance-centric culture to integrating ethical governance, and implementing sophisticated identity management strategies, the following insights delve into key strategies that go beyond the norm, fostering resilience, adaptability, and a proactive stance in the face of regulatory complexities.
What Is IT Compliance in Business?
IT compliance refers to the adherence of information technology (IT) systems, processes, and practices to established standards, regulations, and guidelines. It is part of a larger umbrella term called IT governance, risk, and compliance (GRC). These standards are often set by regulatory bodies, industry associations, or internal organizational policies.
The primary goal of IT compliance is to ensure that organizations operate their IT environments in a secure, reliable, and legally compliant manner. Some IT compliance examples include complying with:
- Telephone Consumer Protection Act (TCPA)
- Health Insurance Portability and Accountability Act (HIPAA)
- EU GDPR (General Data Protection Regulation)
- GLBA (Gramm-Leach-Bliley Act)
Non-compliance with IT regulations can lead to legal consequences, financial losses, and damage to an organization’s reputation. Therefore, businesses invest in IT compliance programs, including Compliance Settings, to mitigate risks and demonstrate their commitment to maintaining a secure and responsible IT environment. Compliance Settings refer to the configuration and enforcement of policies and standards to ensure adherence to regulatory requirements and industry best practices. By implementing Compliance Settings, organizations can proactively address compliance challenges, reduce the likelihood of breaches or violations, and safeguard sensitive data and systems from potential threats.

How to Create an IT Compliance Policy
Creating a compliance policy for IT security compliance involves a systematic process to define, communicate, and enforce rules and guidelines that ensure adherence to legal requirements, industry standards, and organizational expectations. Leveraging compliance automation tools can streamline this process and improve efficiency. Here’s a step-by-step guide on how to create an IT compliance standard policy:
- Identify Applicable Regulations and Standards: Determine the laws, regulations, and industry standards that apply to your organization based on its industry, location, and nature of operations. Examples include data protection laws, industry-specific regulations, and international standards like ISO 27001.
- Establish a Compliance Team: Form a cross-functional team that includes representatives from legal, IT, security, and relevant business units. Assign responsibilities for policy development, enforcement, monitoring, and communication.
- Conduct a Compliance Risk Assessment: Identify potential compliance risks and vulnerabilities within your organization. Assess the impact and likelihood of each risk and prioritize them based on their significance.
- Define Policy Objectives and Scope: Clearly articulate the objectives of the compliance policy. Specify the goals, expectations, and desired outcomes. Define the scope of the policy, including the systems, processes, and personnel it covers.
- Draft Policy Statements and Procedures: Write clear and concise policy statements that outline the organization’s expectations regarding compliance. Include specific procedures and guidelines for implementing the policy, addressing identified risks, and ensuring adherence to regulations.
- Incorporate Legal and Regulatory Requirements: Ensure that the compliance policy explicitly references and aligns with relevant legal and regulatory requirements. Include provisions for regular updates to reflect changes in laws and regulations.
- Gather Stakeholder Input and Feedback: Solicit input from key stakeholders, including employees, managers, legal advisors, and relevant industry experts. Incorporate feedback to enhance the clarity and effectiveness of the policy.
- Review and Approval: Have the compliance policy reviewed by legal counsel to ensure accuracy and alignment with legal requirements. Obtain approval from senior management or the board of directors before finalizing the policy.
- Communication and Training: Develop a communication plan to effectively communicate the policy to all relevant stakeholders. Provide training sessions to employees to ensure understanding of the policy, their roles, and the importance of compliance.
- Establish Monitoring and Enforcement Mechanisms: Define processes for monitoring and auditing compliance with the policy. Specify consequences for non-compliance and establish an enforcement framework.
- Document and Maintain Records: Maintain comprehensive documentation of the compliance policy, including version control. Keep records of training sessions, audits, and any incidents related to non-compliance.
- Regular Review and Update: Schedule regular reviews of the compliance policy to ensure it remains current and aligned with evolving regulations and business needs. Update the policy as needed based on changes in the regulatory landscape or organizational structure.
- Implementation: Roll out the compliance policy across the organization and ensure that employees are aware of its existence, understand its contents, and follow its guidelines.
- Continuous Improvement: Establish a process for continuous improvement by collecting feedback, monitoring effectiveness, and making necessary updates to the policy.

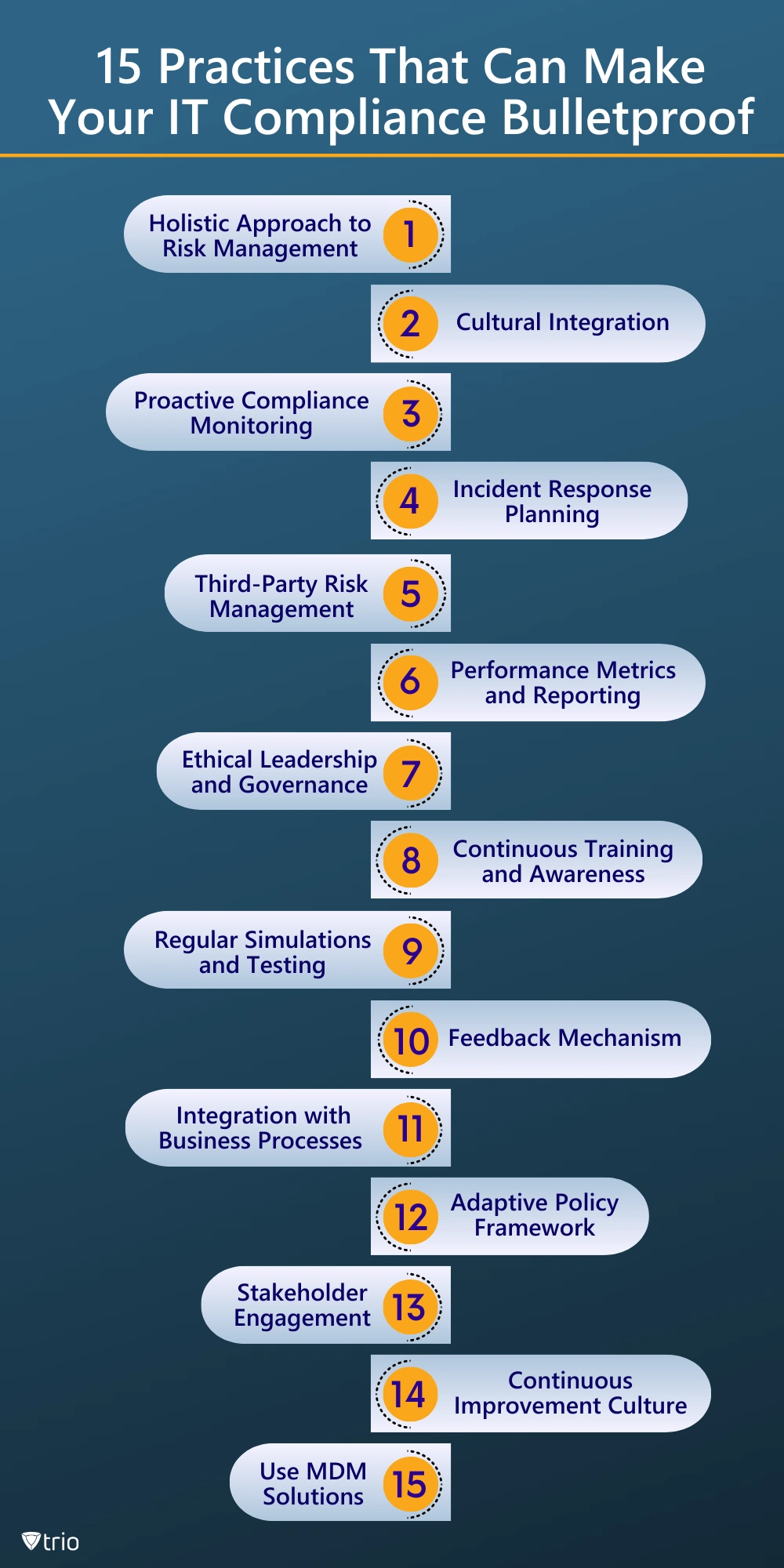
15 Practices That Can Make Your IT Compliance Bulletproof
Though creating an IT compliance policy is an important and necessary step for all organizations, there are some best practices you can adhere to. When it comes to best practices that go beyond the normal process of creating an IT compliance policy, consider the following 15 recommendations:
-
Holistic Approach to Risk Management
Integrate the compliance policy into a broader risk management framework. Consider not only regulatory compliance but also strategic, operational, financial, and reputational risks.
-
Cultural Integration
Foster a culture of compliance throughout the organization. This involves promoting awareness, accountability, and a shared commitment to ethical and compliant behavior.
-
Proactive Compliance Monitoring
Implement proactive monitoring mechanisms to detect compliance issues before they escalate. This could include continuous monitoring, automated alerts, and periodic internal audits.
-
Incident Response Planning
Develop a robust incident response plan that outlines specific steps to be taken in the event of a compliance violation or security incident. Ensure that employees are trained on the plan.
-
Third-Party Risk Management
Extend compliance considerations to third-party vendors and partners. Assess and manage the compliance risks associated with external entities that have access to your organization’s systems or data. For example, your company’s policies on BYOD (Bring Your Own Device), and whether those devices are secure, is what should be assessed in this part.
-
Performance Metrics and Reporting
Define key performance indicators (KPIs) and metrics to measure the effectiveness of your compliance program. Regularly report on these metrics to management and stakeholders.
-
Ethical Leadership and Governance
Emphasize ethical leadership and governance. Leaders should set an example of ethical behavior, and governance structures should support ethical decision-making at all levels of the organization.
-
Continuous Training and Awareness
Beyond initial training, establish a program for continuous education and awareness. Keep employees informed about emerging compliance issues, new regulations, and best practices.
-
Regular Simulations and Testing
Conduct simulations and testing exercises to assess the organization’s response to various compliance scenarios. This helps identify areas for improvement and ensures preparedness.
-
Feedback Mechanism
Establish a feedback mechanism where employees can report compliance concerns or suggest improvements to the compliance program. Ensure confidentiality and non-retaliation for those reporting.
-
Integration with Business Processes
Integrate compliance considerations into various business processes. This includes product development, procurement, and other operational areas where compliance should be a built-in aspect.
-
Adaptive Policy Framework
Design the compliance policy with flexibility to adapt to changing business environments, technologies, and regulatory landscapes. This enables the organization to stay agile and responsive.
-
Stakeholder Engagement
Engage with stakeholders, including customers, investors, and regulatory bodies. Proactively communicate your commitment to compliance and solicit feedback to enhance your program.
-
Continuous Improvement Culture
Cultivate a culture of continuous improvement. The culture in your organization should be so that your emplpyees strive to continuously improve standards and even go above and beyond.
-
Use MDM Solutions
Mobile Device Management (MDM) solutions aid IT compliance by enabling centralized control over mobile devices. The integration of MDM compliance supports IT compliance efforts by addressing challenges associated with mobile device security and data privacy.
Conclusion
As organizations navigate an era where data breaches and regulatory scrutiny are omnipresent, the significance of a comprehensive IT compliance policy cannot be overstated. The journey from regulatory adherence to the incorporation of best practices is pivotal in ensuring not only the protection of sensitive information but also the long-term viability of the business.
By embracing a holistic approach to risk management, cultivating a culture of continuous improvement, and integrating compliance into the fabric of business operations, organizations can not only meet regulatory requirements but also position themselves as ethical leaders in the digital realm.
In the pursuit of IT compliance excellence, these advanced best practices serve as a compass, guiding organizations toward a future where resilience and ethical conduct are not just ideals but ingrained elements of their operational DNA. Additionally, incorporating compliance training best practices ensures that employees are equipped with the knowledge and skills to navigate complex regulatory landscapes effectively, reducing the risk of non-compliance and fostering a culture of compliance throughout the organization.
An MDM solution we recommend you try out is Trio. Trio allows you to automate processes, provide security features, and enable secure and controlled remote access to resources. You can try out Trio’s free demo for your organization today.
Get Ahead of the Curve
Every organization today needs a solution to automate time-consuming tasks and strengthen security.
Without the right tools, manual processes drain resources and leave gaps in protection. Trio MDM is designed to solve this problem, automating key tasks, boosting security, and ensuring compliance with ease.
Don't let inefficiencies hold you back. Learn how Trio MDM can revolutionize your IT operations or request a free trial today!