The modern workforce is constantly connected, accessing corporate data on a variety of devices from anywhere, at any time. This presents IT administrators with the critical task of ensuring the security of this ever-expanding mobile landscape. Mobile Device Management (MDM) and Mobile Application Management (MAM) are two effective tools that can aid in this endeavor.
MDM solutions offer comprehensive control over entire devices, allowing you to enforce security policies, manage apps, and remotely wipe data if necessary. MAM, on the other hand, focuses on securing enterprise applications and the sensitive information they contain, even on employee-owned devices.
Choosing the right solution depends on your specific needs and objectives. This article will delve into the world of MDM vs. MAM, exploring their benefits and key differences. Ultimately, it aims to help you decide which approach best suits your organization’s mobile security strategy.
What Is Mobile Device Management (MDM)?
Mobile Device Management (MDM) is a set of tools that allows companies to control and secure the smartphones, tablets, and laptops their employees use for work. This can include company-issued devices or even personal devices that employees use to access work email or files.
Companies use MDM software for two main reasons: security and control. With MDM, they can make sure that devices meet minimum security standards, like having strong passwords and up-to-date software. MDM can also allow them to remotely wipe a lost or stolen device, so no company data is at risk.
Benefits of MDM
MDM offers many advantages for organizations seeking to secure their mobile environment and empower a productive mobile workforce. Let’s delve into some of the key benefits:
Fortified Security
MDM goes beyond basic password enforcement. It allows you to configure complex password requirements with minimum character lengths, mandatory special character inclusion, and regular password changes. Additionally, MDM enforces encryption standards for data at rest and in transit. This ensures that even if a device is compromised, sensitive information remains encrypted and unreadable.
Furthermore, MDM empowers granular access controls. You can restrict access to specific corporate resources based on user roles and device types. For example, a sales representative might only need access to customer relationship management (CRM) software on their phone. On the other hand, a senior manager might require access to a wider range of applications, including financial reports and sensitive documents. This minimizes the potential for unauthorized access to sensitive information and reduces the overall attack surface.
Simplified App Management
MDM streamlines the process of deploying, distributing, and updating approved applications across the organization’s mobile devices. Imagine that your company is rolling out a new custom sales app for your team. With MDM, you can easily push the app to all authorized devices simultaneously, eliminating the need for manual installation on each device. This not only saves IT time and resources but also ensures consistency and reduces the risk of errors.
Furthermore, MDM allows for restricting unauthorized apps. You can create a blacklist of applications that are deemed a security risk or violate company policy. This prevents users from installing or using these apps on their work devices, further enhancing the overall security posture of your mobile environment. For instance, you might restrict file-sharing applications that could be used to leak sensitive data or social media apps that could introduce malware threats.
Enhanced Data Loss Prevention
The remote wipe capability of MDM proves invaluable in the event of a lost or stolen device. With a few clicks, IT admins can remotely erase all corporate data from the device. This prevents unauthorized access and mitigates the risk of data leaks. Data loss prevention is particularly crucial for organizations that handle sensitive information such as customer data, financial records, or intellectual property.
This feature not only protects sensitive information but also helps the organization comply with data privacy regulations. Additionally, as we already mentioned, MDM can help prevent accidental data loss by prompting users to encrypt sensitive data before sharing it outside the organization.
Increased Productivity
MDM fosters a more productive mobile workforce by enabling features like secure email, calendar, and document synchronization across devices. This ensures users have consistent access to the information they need, regardless of their location or the device they’re using.
Imagine a salesperson on the road who needs to access the latest customer contact information or a doctor who needs to review patient charts while traveling between appointments. With MDM-enabled synchronization, they can access this critical information seamlessly from their mobile devices, improving their efficiency and responsiveness. By providing easy access to essential work tools and information, MDM empowers employees to be productive and efficient even when they are outside the office.

Reduced IT Support Burden
MDM automates many of the mundane tasks associated with mobile device management, freeing up IT staff to focus on more strategic initiatives. Automated app distribution, configuration management, and security policy enforcement significantly reduce the IT support burden associated with managing many mobile devices.
For instance, imagine an organization with hundreds of employees using various mobile devices. Manually configuring security settings, deploying apps, and troubleshooting issues on each device would be a time-consuming and resource-intensive task. With MDM, these tasks can be automated. This will allow IT staff to focus on more critical projects like improving network security or developing new mobile solutions for the business.
What Is Mobile Application Management (MAM)?
Mobile Application Management (MAM) differs from MDM by focusing solely on securing corporate data within specific work applications, regardless of the device they reside on. This targeted approach proves valuable for organizations with Bring Your Device (BYOD) policies, where employees use personal smartphones and tablets for work activities.
MAM safeguards sensitive information within approved corporate applications, even on devices that IT may not have complete control over. By implementing containerization technology, MAM essentially creates a secure enclave within the application. It isolates corporate data from personal information and ensures its protection.
Benefits of MAM
In the case of MDM vs. MAM, the latter offers several advantages for organizations seeking to secure corporate data within specific work applications on employee devices. It’s particularly effective in resolving BYOD challenges. Let’s explore some key benefits:
Enhanced User Privacy
Compared to the comprehensive control MDM exerts over entire devices, MAM focuses solely on the security of enterprise applications. This means employees retain more privacy on their devices. That’s because MAM doesn’t interfere with non-work apps or data.
An MDM solution might restrict employees from downloading certain games or music apps, while MAM wouldn’t touch those functionalities. This fosters a sense of trust and can be crucial for fostering BYOD (Bring Your Device) program acceptance. Employees are more likely to participate in a BYOD program if they feel their personal information and habits are not being monitored.
Greater Flexibility
MAM software allows for more granular control within specific apps. IT teams can implement security policies like data encryption, copy/paste restrictions, and remote wipe capabilities solely for work data within the app, without affecting personal data or functionalities.
Imagine that an employee uses a note-taking app for both work and personal purposes. MAM can ensure that only the work notes section within the app is encrypted and can be remotely wiped if the device is lost or stolen. At the same time, the employee’s notes remain secure and accessible. This targeted approach offers a more flexible security solution.
More Control Depth
MDM and MAM offer different levels of control when it comes to mobile security. MDM prioritizes broad strokes, managing the entire device. It resembles securing your whole house with an alarm system. You know everything inside is protected, but there’s no distinction between the valuables in the vault and the groceries in the kitchen.
MAM security offers a more nuanced approach, focusing on specific applications. It’s like having a separate security system for your home office. You can lock down sensitive documents while allowing free access to personal files on your computer.
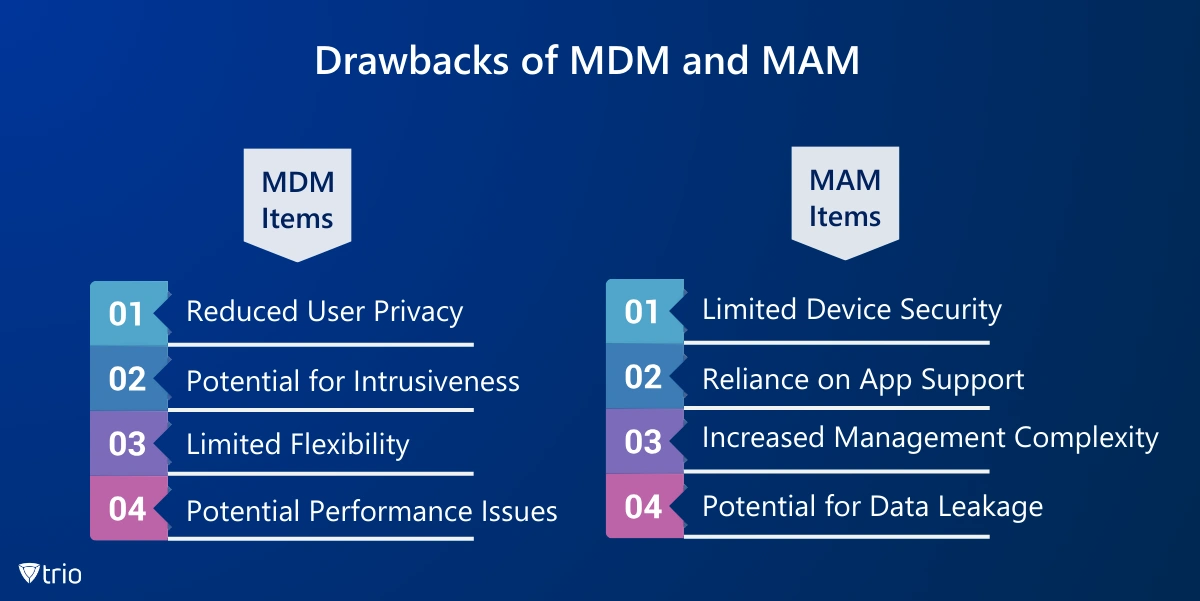
Final Word: Choosing the Right Solution
In the battle of MDM vs. MAM, there seems to be no apparent winner. Selecting the optimal solution between MDM and MAM hinges on your organization’s specific needs and priorities. If your organization requires comprehensive control over every device accessing your corporate network, then MDM is the ideal choice. If you have a BYOD policy, want to secure work data within specific apps on employee devices, and respect their privacy, then choose MAM.
Overall, remember that MDM and MAM are not mutually exclusive solutions. Combining them can offer the best of both worlds: comprehensive device management with enhanced application-level security. This layered approach significantly strengthens your organization’s overall mobile security posture.
See Trio in Action: Get Your Free Trial Now!
If you’re seeking to implement a robust MDM solution for managing and securing your organization’s mobile devices, consider Trio. Trio offers a comprehensive suite of features, including remote control, device enrollment, application management, security policy enforcement, and remote wipe capabilities. It caters to businesses of all sizes and provides a user-friendly interface for seamless device management.
Sign up for a Free Demo today and see how Trio can help you unlock the full potential of mobile security in your organization!




