As technology continues to evolve at a rapid pace, managing devices across an organization can quickly become a daunting task for IT administrators. With the growing complexity of digital ecosystems, ensuring security, compliance, and efficiency can feel like juggling endless responsibilities. Enter Mobile Device Management (MDM) – a powerful solution that empowers IT teams to streamline device management, safeguard company data, and stay ahead of emerging tech challenges.
The demand for MDM solutions has skyrocketed in recent years, driven by three key trends: the rise of remote work, the adoption of Bring Your Own Device (BYOD) policies, and growing cybersecurity concerns. With employees working from anywhere, on various devices, ensuring data security and seamless operations has become a top priority. As a result, MDM software vendors are continuously evolving to offer better security, automation, and ease of management. MDM not only simplifies these tasks but also provides peace of mind by protecting sensitive information and keeping devices running smoothly.
In this blog, we’ll break down the essentials of MDM, why it matters for your organization, and how it can make IT admin’s job easier.
What is Mobile Device Management (MDM)?
MDM is a set of technologies and practices that allow IT administrators to manage and secure mobile devices, such as smartphones, tablets, and laptops, from a central platform. In simple terms, it’s like having a remote control for all the mobile devices in your organization. With MDM, you can enforce security policies, install or update apps, track device locations, and even wipe data if a device is lost or stolen—all without needing physical access to the device.
MDM is often compared to Mobile Application Management (MAM), but the two serve different purposes. While MDM focuses on managing entire devices—enforcing security settings, controlling access, and ensuring compliance—MAM specifically manages applications and their data without taking full control of the device.
Both MDM and MAM fall under Enterprise Mobility Management (EMM), which is a broader framework for managing not just devices but also apps, content, and security policies. EMM provides IT teams with a centralized way to secure and streamline mobile operations, whether employees are using company-owned or personal devices.
Additionally, MDM fits within Unified Endpoint Management (UEM), which takes mobility management a step further by extending control to desktops, IoT devices, and other endpoints. UEM consolidates device management into a single platform, simplifying IT administration across an organization.
In some cases, MDM also plays a role within Remote Monitoring and Management (RMM) solutions. RMM tools are designed for IT service providers to remotely monitor, troubleshoot, and maintain devices, often incorporating MDM features to enhance security and compliance.
In summary, MDM manages mobile devices, MAM secures only apps and data, both fall under EMM, UEM expands management to all endpoints, and RMM enhances remote monitoring with MDM capabilities.
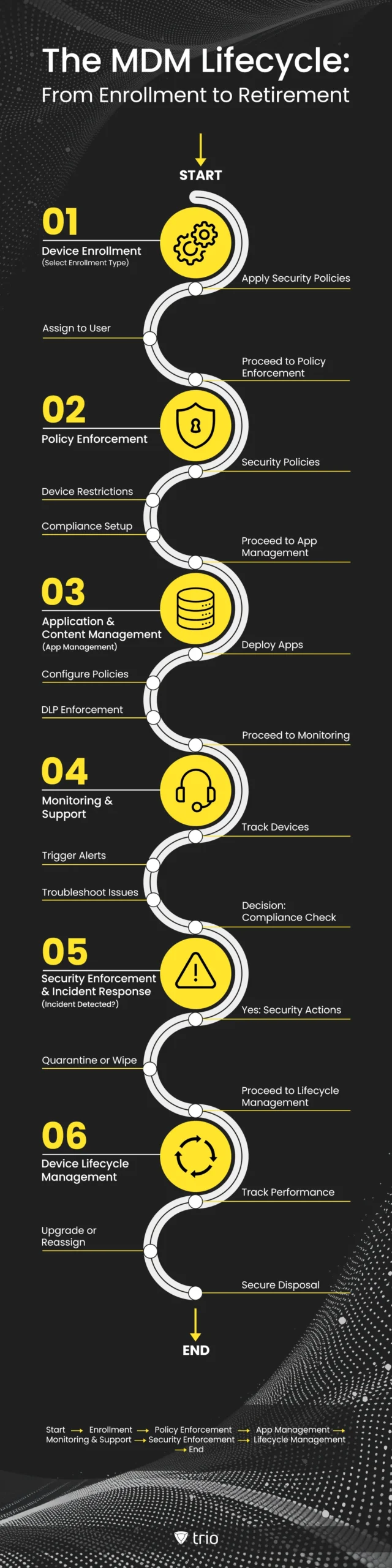
How Does MDM Work?
While MDM might sound complex, its implementation can be broken down into clear, manageable steps.
Step 1: Define Your Needs
The implementation process begins with defining the organization’s requirements and objectives. IT teams must determine which devices need management (iOS, Android, Windows, etc.), what security and compliance measures should be enforced, and how access control and data protection policies should be structured.
Step 2: Choose an MDM Solution
Once the requirements are clear, the next step is choosing an MDM solution that best fits the organization’s needs. This decision involves selecting between cloud-based or on-premises deployment, ensuring compatibility with existing IT infrastructure, and evaluating features such as policy enforcement, app management, and security controls. Scalability is another key factor, as businesses must ensure the solution can support growth, whether by adding more devices, integrating with new platforms, or expanding to multiple locations. Additionally, cost considerations play a significant role, as organizations need to balance the upfront investment, licensing fees, and ongoing maintenance costs with the expected benefits and long-term value of the MDM solution.
Step 3: Set Up the MDM Server
After selecting an MDM provider, the IT team sets up the MDM server, configuring administrative roles, integrating the solution with enterprise systems like Active Directory or email servers, and preparing for device enrollment.
If migrating from another MDM solution, ensure the new platform supports an efficient migration process to avoid downtime and ensure all devices and policies are transferred correctly.
Step 4: Enroll Devices
After setting up the server, the next step is MDM enrollment, where devices are registered with the system for remote management. This process varies depending on the device type:
- Corporate-Owned Devices: These can be pre-configured and enrolled automatically before being handed to employees.
- BYOD (Bring Your Own Device): Employees can enroll their personal devices by downloading an MDM agent or app and following the setup instructions.
During enrollment, devices are “registered” with the MDM server, allowing IT admins to manage them remotely.
Step 5: Configure Policies and Profiles
Once devices are enrolled, you can define and apply policies and profiles. These are rules and settings that control how devices operate. For example:
- Security Policies: Require strong passwords, enable encryption, or set up biometric authentication.
- Network Settings: Configure Wi-Fi, VPN, or email access and restrict unauthorized access to corporate data.
- App Management: IT teams deploy, update, and remove apps remotely while enforcing app whitelisting or blacklisting to prevent security risks.
Step 6: Monitor and Manage Devices
With devices enrolled and policies in place, the MDM system allows you to monitor and manage them in real time. You can:
- Track device locations.
- Track device status and security posture.
- Push software updates or app installations.
- Automate actions, such as locking or wiping compromised devices.
- Set up alerts for policy violations, jailbroken/rooted devices, or unauthorized access.
Step 7: Provide Ongoing Support
Finally, MDM is not a one-time setup—it requires ongoing maintenance. Regularly review and update policies, address employee concerns, and ensure the system scales as your organization grows. Many MDM solutions also offer analytics to help you identify trends or potential issues. Continuous maintenance and support ensure the MDM solution remains effective.
Benefits of MDM: Why It’s a Game-Changer for IT Admins
Implementing an MDM solution brings a wide range of benefits to organizations, especially in today’s remote and mobile-driven work environment. Here’s a closer look at how MDM can make a significant difference:
1. Enhanced Security
Security is one of the biggest challenges for IT admins, and MDM provides powerful tools to address it:
- Device Encryption: MDM ensures that sensitive data on devices is encrypted, protecting it from unauthorized access.
- Remote Wipe: If a device is lost or stolen, you can remotely wipe all data to prevent breaches. This is especially important for BYOD policies, where personal and work data coexist.
- Compliance: MDM helps enforce compliance with industry regulations (like GDPR or HIPAA) by ensuring devices meet security standards and policies.
2. Improved Productivity
MDM doesn’t just secure devices—it also helps employees work more efficiently:
- Device Monitoring: IT admins can track device performance and troubleshoot issues remotely, reducing downtime.
- App Management: MDM allows you to push necessary apps to devices, update them automatically, and block unauthorized or risky apps. This ensures employees have the tools they need to stay productive.
- Seamless Updates: Software and security updates can be rolled out automatically, keeping devices up-to-date without requiring manual intervention.
3. Cost Savings
MDM can also lead to significant cost savings for organizations:
- Better Resource Allocation: With centralized management, IT teams can allocate resources more effectively, reducing the need for repetitive manual tasks.
- Reduced IT Workload: Automated processes like policy enforcement, app deployment, and updates free up IT staff to focus on strategic initiatives rather than day-to-day troubleshooting.
- Lower Risk of Data Breaches: By preventing security incidents, MDM helps avoid costly fines, legal fees, and reputational damage.
Benefits of MDM: Why It’s a Game-Changer for IT Admins
Implementing an MDM solution brings a wide range of benefits to organizations, especially in today’s remote and mobile-driven work environment. Here’s a closer look at how MDM can make a significant difference:
1. Enhanced Security
Security is one of the biggest challenges for IT admins, and MDM provides powerful tools to address it:
- Device Encryption: MDM ensures that sensitive data on devices is encrypted, protecting it from unauthorized access.
- Remote Wipe: If a device is lost or stolen, you can remotely wipe all data to prevent breaches. This is especially important for BYOD policies, where personal and work data coexist.
- Compliance: MDM helps enforce compliance with industry regulations (like GDPR or HIPAA) by ensuring devices meet security standards and policies.
2. Improved Productivity
MDM doesn’t just secure devices—it also helps employees work more efficiently:
- Device Monitoring: IT admins can track device performance and troubleshoot issues remotely, reducing downtime.
- App Management: MDM allows you to push necessary apps to devices, update them automatically, and block unauthorized or risky apps. This ensures employees have the tools they need to stay productive.
- Seamless Updates: Software and security updates can be rolled out automatically, keeping devices up-to-date without requiring manual intervention.
3. Cost Savings
MDM can also lead to significant cost savings for organizations:
- Better Resource Allocation: With centralized management, IT teams can allocate resources more effectively, reducing the need for repetitive manual tasks.
- Reduced IT Workload: Automated processes like policy enforcement, app deployment, and updates free up IT staff to focus on strategic initiatives rather than day-to-day troubleshooting.
- Lower Risk of Data Breaches: By preventing security incidents, MDM helps avoid costly fines, legal fees, and reputational damage.
Possible MDM Challenges and How to Overcome Them
While MDM offers numerous benefits, implementing and managing it can come with its own set of challenges. Here’s a look at some common hurdles IT admins face and practical solutions to overcome them:
1. BYOD Security Risks
Bring Your Own Device (BYOD) policies are popular for their flexibility and cost savings, but they also introduce security risks. Personal devices may lack the same level of security as corporate-owned ones, and employees might use unsecured networks or download risky apps.
Solution
Implement strong BYOD policies and enforce them through MDM. For example:
- Require devices to meet minimum security standards (e.g., encryption, passcodes).
- Use containerization to separate work data from personal data.
- Regularly audit devices for compliance and block non-compliant ones.
2. Privacy Concerns
Employees may feel uncomfortable with IT admins having access to their personal devices, especially when it comes to monitoring or controlling apps and data. This can lead to resistance or low adoption rates.
Solution
A well-crafted MDM policy can strike a balance between security and privacy. Transparency is key—clearly define what IT can and cannot do with the MDM system. For example:
- Limit monitoring to work-related apps and data.
- Avoid accessing personal files or apps.
- Communicate the purpose of MDM (e.g., protecting company data) and how it benefits employees.
3. Complexity of Management
Managing a large number of devices, especially across different platforms (iOS, Android, Windows), can be overwhelming. Without the right tools, IT admins may struggle to keep up with updates, policies, and troubleshooting.
Solution
Choose a user-friendly MDM platform that simplifies management. Look for features like:
- A centralized dashboard for easy monitoring and control.
- Automation for tasks like software updates and policy enforcement.
- Cross-platform support to manage all devices from a single interface.
Most Essential MDM Features
When choosing an MDM solution, it’s important to focus on features that deliver the most value for your organization. Here are four essential MDM features, along with examples of how they can be used:
1. Device Tracking & Remote Wipe
This feature allows IT admins to track the location of a device and remotely wipe its data if it’s lost, stolen, or compromised.
Real-World Example
Imagine an employee leaves their company-issued tablet in a taxi. Using MDM, the IT team can track the device’s location in real time. If recovery isn’t possible, they can remotely wipe all sensitive data to prevent it from falling into the wrong hands. This ensures that confidential company information remains secure, even if the device is gone.
2. App & Content Management
MDM enables IT admins to control which apps are installed on devices, push necessary apps, and manage updates. It also allows for the secure distribution of work-related content, ensuring employees have access to the latest documents, policies, and files without relying on unsecured sharing methods.
Real-World Example
A sales team needs access to a new CRM app to manage client interactions. Instead of asking each employee to download and configure the app manually, the IT team uses MDM to push the app to all devices automatically. Alongside app deployment, they also distribute essential sales materials, such as pricing sheets and contracts, ensuring employees always have up-to-date resources at their fingertips. Additionally, they restrict access to unauthorized apps and prevent the use of unsecured file-sharing services, maintaining both security and consistency across the team.
3. Policy Enforcement & Compliance
MDM allows IT admins to enforce security policies, such as requiring strong passwords, enabling encryption, and restricting access to certain features or networks. MDM configuration plays a key role in ensuring policies are correctly applied and consistently maintained across all managed devices. It helps organizations stay compliant with industry regulations while reducing security risks.
Real-World Example
A healthcare organization must comply with HIPAA regulations to protect patient data. Using MDM, the IT team enforces policies like mandatory device encryption, automatic screen locks, and restricted access to unsecured Wi-Fi networks. Regular compliance reports are generated to demonstrate adherence during audits.
4. Automated Provisioning
Automated provisioning simplifies the setup of new devices by configuring them with the necessary settings, apps, and policies as soon as they are enrolled in the MDM system.
Real-World Example
A company hires 50 new employees and provides them with company-issued smartphones. Instead of manually setting up each device, the IT team uses MDM to automate the process. As soon as a device is powered on, it’s automatically configured with email accounts, Wi-Fi settings, and required apps. This reduces setup time and ensures all devices are ready to use from day one.

Managing Different Devices with MDM: Best Practices for Every Platform
MDM isn’t a one-size-fits-all solution. Different types of devices—whether company-owned, BYOD, or specialized—require tailored strategies to ensure security, efficiency, and compliance. Here’s a breakdown of how to manage various devices effectively with MDM:
1. Company-Owned vs. BYOD Devices
Whether your organization relies on company-owned or BYOD devices, understanding the distinct best practices for each is essential. A strong MDM strategy should differentiate between the two to ensure both security and usability.
Company-Owned Devices
- Best Practices:
- Enroll devices during initial setup to ensure they’re configured with the right policies and apps from the start.
- Use strict security measures, such as mandatory encryption, regular updates, and remote wipe capabilities.
- Monitor device usage to ensure compliance with company policies.
BYOD (Bring Your Own Device)
- Best Practices:
- Implement MDM containerization to separate work data from personal data, ensuring employee privacy.
- Enforce minimum security requirements, such as passcodes and encryption, for devices accessing company resources.
- Provide clear guidelines on acceptable use and regularly audit devices for compliance.
2. iOS and macOS
Apple devices are widely used in businesses due to their reliability and security features. To ensure optimal management, it’s essential to choose the best Apple MDM solution that aligns with your organization’s needs.
- Best Practices:
- Use Apple Business Manager (ABM) or Apple School Manager (ASM) to streamline device enrollment and app distribution.
- Leverage built-in security features like Touch ID, Face ID, and automatic updates.
- Deploy configuration profiles to enforce Wi-Fi, email, and VPN settings.
- Use app whitelisting and blacklisting to control which apps can be installed.
3. Android
Android devices are highly customizable but can vary widely in terms of hardware and software. To manage them effectively, it’s crucial to use the right Android management software to ensure security and consistency across all devices. Here’s how to manage them effectively:
- Best Practices:
- Use Android Enterprise to manage devices, apps, and configurations.
- Enforce security policies like encryption, screen locks, and Google Play Protect for malware detection.
- Utilize work profiles to separate personal and work data on BYOD devices.
- Push updates and patches to ensure devices are running the latest software.
4. Windows
Windows devices are a staple in many organizations, especially for desktop and laptop users. To manage them effectively, it’s important to leverage the right tools, such as MDM for Windows, to ensure security and efficiency across all devices. Here’s how to manage them effectively:
- Best Practices:
- Use MDM to enforce BitLocker encryption and Windows Defender for enhanced security.
- Automate software updates and patch management to keep systems secure.
- Configure network settings, such as Wi-Fi and VPN, for remote workers.
- Monitor device performance and troubleshoot issues remotely.
5. IoT & Specialized Devices
IoT (Internet of Things) devices, such as smart sensors, kiosks, or medical equipment, require unique management approaches:
- Best Practices:
- Use MDM to monitor device health and performance in real time.
- Enforce security measures like firmware updates and network restrictions.
- Restrict access to sensitive data or systems connected to IoT devices.
- Use geofencing to ensure devices operate only in designated areas.
MDM Use Cases: Tailoring Solutions for Different Industries
MDM is a versatile tool that can benefit organizations of all sizes and across various industries. Here’s how MDM is being used in different sectors, from small businesses to healthcare and retail:
Small Businesses vs. Enterprises
Whether you’re running a small business or a large enterprise, the need for a robust MDM solution is essential. Why would you need an MDM for your small business? Well, small businesses often lack dedicated IT resources, making device management and security even more crucial. An MDM solution helps streamline device management, enforce security policies, and ensure compliance without the need for a large IT team. It allows small businesses to focus on growth and innovation, while providing security and operational efficiency across their devices.
For large enterprises, managing a wide variety of devices, applications, and users across multiple locations requires centralized control. MDM enables enterprises to enforce security policies, automate updates, and manage thousands of devices from a single platform. This reduces risks, optimizes resources, and eases the burden on IT teams, helping enterprises stay secure and compliant at scale.
Education
In the education sector, device management plays a key role in maintaining a safe and productive environment. With MDM for schools, administrators can manage devices remotely, ensuring that students have access to the necessary tools while maintaining security. Some of the MDM solutions in education provide advanced student safety features, offering schools a smart way to manage devices while ensuring student safety both online and offline. Real-time monitoring and robust security measures can ensure a safe and effective learning experience.
Healthcare
For healthcare organizations, protecting patient data is crucial. The Health Insurance Portability and Accountability Act (HIPAA) establishes critical standards for safeguarding sensitive patient information. By adhering to HIPAA’s Minimum Necessary Standard, healthcare organizations can ensure they are protecting patient data effectively. To stay compliant, using a HIPAA compliance checklist is essential for keeping up with privacy regulations, which ultimately helps maintain patient trust. Moreover, implementing a HIPAA-compliant MDM solution ensures that all devices are managed in accordance with these regulations. With the right MDM solution in place, healthcare providers can enforce encryption, protect sensitive data, and remotely wipe devices when necessary to mitigate security risks.
Retail
In the retail sector, managing POS (Point of Sale) devices is crucial for both operational efficiency and security. With POS device management through an MDM solution, retailers can ensure that devices are always up-to-date, secure, and functioning properly. This not only minimizes downtime but also helps protect sensitive customer data from breaches. Centralized management of POS devices makes it easier for retailers to monitor and manage devices across multiple locations, ensuring a seamless customer experience and enhanced security.
Best MDM Software: Comparison Guide
Choosing the right MDM solution can be overwhelming, given the variety of options available. To help you make an informed decision, we’ve compared some of the top MDM tools, including Trio, based on features, business size, industry suitability, pros and cons, and pricing models.
Feature Comparison Table of Top MDM Solutions
| Attribute | Trio | Jamf | Kandji | Mosyle | SimpleMDM | Hexnode |
|---|---|---|---|---|---|---|
| Supported OS | macOS, iOS, iPadOS, tvOS, Android, Windows | macOS, iOS, iPadOS, tvOS | macOS, iOS, iPadOS, tvOS | macOS, iOS, iPadOS, tvOS | macOS, iOS, iPadOS | macOS, iOS, Android, Windows |
| Pricing | Custom pricing (contact for details) | Starts at $8/mo/Mac, $4/mo/other | Starts at $4/mo/device | $1.50 per iPhone/iPad, $3 per Mac | Starts at $4/device | Starts at $1/device |
| Ease of Use and Setup | Intuitive UI, easy setup for SMBs | Steep learning curve, for experienced admins | User-friendly with no coding required | CDN for custom packages, complex for new users | Easy to set up with cloud management | Simple interface, easy onboarding |
| Device Management Capabilities | Multi-device management, App deployment, Remote wipe, BYOD support | Leverages DEP, Device automation, Device restrictions | Device automation, real-time monitoring, configuration management | Automated battery alerts, device locking, BYOD support | Device management, app deployment, security profiles | Device control, app management, real-time tracking |
| Security Features | Full disk encryption, Remote wipe, Compliance with CIS, NIST, SOC2 | ISO 27001, Threat monitoring, Encryption | SOC2, device-level security, app security, encryption | Full disk encryption, SOC2, CIS mapping | Encryption, secure app management, remote wipe | Advanced security controls, compliance support |
| Integration Options | Google, Microsoft 365, Okta, Ping | AWS, Okta, Google, Intune, ServiceNow | AWS, Okta, Microsoft, Google | Google, Microsoft 365, Okta, Ping | Google, Microsoft 365, Okta, G Suite | AWS, Google, Microsoft, Okta, ServiceNow |
Top 5 Solutions and Their Pros & Cons
With many options available, choosing the right MDM solution depends on your organization’s needs. Below are the top 5 MDM solutions, each with its unique advantages and potential drawbacks, to help you make an informed decision.
1. Trio
- Pros:
- Affordable, cost-effective solution for SMBs.
- Supports Windows, macOS, iOS, and Android.
- User-friendly interface, easy to manage.
- Scalable as your business grows.
- Strong security features (remote lock/wipe).
- Cons:
- Fewer features for large enterprises.
- Smaller user base.
2. Jamf
- Pros:
- Best for Apple devices (macOS & iOS).
- Extensive deployment and security features.
- Enterprise-ready.
- Cons:
- Expensive pricing.
- Limited to Apple devices.
3. Kandji
- Pros:
- Strong automation tools.
- Excellent Apple device management.
- Comprehensive security and compliance features.
- Cons:
- Apple-only solution.
- High cost, especially for SMBs.
4. Mosyle
- Pros:
- Affordable, with a free version for education.
- User-friendly interface.
- Strong Apple device management.
- Cons:
- Limited to Apple devices.
- Fewer features for large enterprises.
5. Hexnode
- Pros:
- Supports a wide range of devices (Windows, macOS, iOS, Android).
- Comprehensive features (remote wipe, kiosk mode, etc.).
- Scalable for SMBs and large enterprises.
- Cons:
- Steeper learning curve.
- Higher cost for SMBs.
The Future of MDM and Emerging Trends
As technology evolves, so does MDM. The future of MDM is being shaped by tech advancements. Here’s a look at the trends that are transforming MDM and what they mean for IT admins:
AI & Automation in MDM
AI and automation are revolutionizing MDM by making device management smarter, faster, and more efficient. These technologies enable proactive problem-solving, reduce manual workloads, and enhance decision-making.
Key Trends
- Predictive Analytics: AI can analyze device performance data to predict potential issues, such as hardware failures or security vulnerabilities, before they occur.
- Automated Remediation: AI-powered MDM solutions can automatically resolve common issues, such as applying patches, updating software, or quarantining compromised devices.
- Behavioral Analysis: AI can monitor user behavior to detect anomalies, such as unusual login attempts or data access patterns, and trigger alerts or actions to prevent security breaches.
Why It Matters
AI and automation not only streamline device management but also enhance security and productivity. By leveraging these technologies, IT admins can focus on strategic initiatives rather than routine tasks.
Zero Trust Security Model
The Zero Trust security model is becoming a foundation of modern cybersecurity. Unlike traditional security models that assume everything inside a network is safe, Zero Trust operates on the principle of “never trust, always verify.” This approach is particularly relevant for MDM, where devices often operate outside traditional network perimeters.
Key Trends
- Device Authentication: Every device must be authenticated before accessing company resources, regardless of its location. MDM solutions are integrating multi-factor authentication (MFA) and biometric verification to strengthen this process.
- Least Privilege Access: Devices and users are granted only the minimum level of access required to perform their tasks. MDM systems enforce this by applying granular access controls based on roles, locations, and device compliance.
- Continuous Monitoring: Zero Trust requires constant monitoring of device activity. MDM solutions are incorporating real-time analytics to detect and respond to threats instantly.
Why It Matters
With the rise of remote work and BYOD policies, the Zero Trust model ensures that devices are secure, even when they’re outside the corporate network. MDM plays a critical role in implementing and enforcing Zero Trust principles.
Integration with IoT and Edge Computing
As IoT devices and edge computing become more prevalent, MDM is expanding to manage these endpoints. This includes everything from smart sensors to industrial equipment, which often operate in remote or harsh environments.
Key Trends:
- Unified Endpoint Management (UEM): MDM is evolving into UEM, which manages not just mobile devices but also IoT and edge devices. This provides a single platform for all endpoints, simplifying management and improving visibility.
- Edge Security: MDM solutions are incorporating features to secure IoT devices at the edge, such as firmware updates, network segmentation, and anomaly detection.
Why It Matters
The growing number of IoT devices increases the attack surface for organizations. MDM solutions that can manage and secure these devices are essential for maintaining operational efficiency and security.
Enhanced User Experience
As employees demand more flexibility and ease of use, MDM solutions are focusing on improving the user experience. This includes simplifying enrollment processes, providing self-service options, and ensuring seamless access to resources.
Key Trends:
- Self-Service Portals: Employees can enroll their devices, troubleshoot issues, and access resources without IT intervention.
- Seamless Integration: MDM solutions are integrating with collaboration tools to provide a unified experience.
Why It Matters
A positive user experience increases adoption rates and reduces resistance to MDM policies, making it easier for IT admins to enforce security and compliance.

Conclusion
Mobile Device Management (MDM) is no longer a luxury—it’s a necessity for organizations of all sizes and industries. It serves as a centralized tool to manage, secure, and monitor mobile devices, apps, and data, addressing the growing demands of remote work, BYOD policies, and cybersecurity concerns. With essential features like device tracking, app management, policy enforcement, and automated provisioning, MDM ensures businesses stay secure, productive, and compliant. Industries such as education, healthcare, retail, and enterprises all benefit from tailored MDM solutions that meet their unique needs. As we’ve seen, MDM not only solves current challenges but also prepares organizations for future trends, including AI, automation, Zero Trust security, and IoT integration.
Take the Next Step with Trio
Whether you’re a small business, a growing enterprise, or part of a specialized industry like education or healthcare, Trio is here to help you streamline IT management and enhance security. Our tailored MDM solution is designed to meet your organization’s specific needs, providing seamless management and robust protection. Experience the benefits of Trio’s MDM solution firsthand with a no-obligation free trial, and see how it can transform your business. If you’re ready to take the next step, our team of experts is here to guide you in selecting the perfect MDM solution for your organization, ensuring a smooth and secure IT environment.
See Trio in Action: Get Your Free Trial Now!
The right MDM solution can make all the difference in securing your devices, streamlining operations, and empowering your team. Don’t wait—take the first step toward a more secure and efficient future today.
Get Ahead of the Curve
Every organization today needs a solution to automate time-consuming tasks and strengthen security.
Without the right tools, manual processes drain resources and leave gaps in protection. Trio MDM is designed to solve this problem, automating key tasks, boosting security, and ensuring compliance with ease.
Don't let inefficiencies hold you back. Learn how Trio MDM can revolutionize your IT operations or request a free trial today!