In the dynamic landscape of IT infrastructure management, the advent of Remote Monitoring and Management (RMM) tools has revolutionized the way organizations oversee and support their digital ecosystems. RMM tools, with their array of functionalities, empower IT administrators and managed service providers (MSPs) to remotely monitor, manage, and maintain clients' IT infrastructure, systems, and endpoints. In fact, according to Kaseya in 2019, over 50% of MSPs believed their RMM tools to be their most precious application. This article delves into the essence of RMM software, showing their significance in modern IT operations and explaining the benefits they have for organizations striving for efficient and proactive management of their technological assets.
What are RMM Tools?
RMM (Remote Monitoring and Management) tools are software solutions designed to enable IT administrators and managed service providers (MSPs) to remotely monitor, manage, and maintain clients' IT infrastructure, systems, and endpoints. These tools offer a suite of functionalities including remote monitoring, remote management, security monitoring, automation, alerting, reporting, and asset management. By leveraging RMM solutions, IT professionals can efficiently oversee and support their clients' IT environments without the need for physical presence. The benefits of RMM business solutions in managing IT infrastructure include:
- Improved Efficiency: RMM tools automate repetitive tasks and streamline workflows, enabling administrators to manage IT infrastructure more efficiently and effectively.
- Proactive Monitoring and Maintenance: With real-time monitoring and alerts, administrators can proactively identify and address issues before they impact productivity or disrupt operations.
- Cost Savings: By reducing the need for on-site support and minimizing downtime, RMM tools help organizations save money on IT maintenance and support costs. You may be able to find free RMM tools such as trial versions to test these solutions first before getting them for your organization.
- Enhanced Security: RMM tools enable administrators to monitor for security threats and vulnerabilities, implement security measures, and ensure compliance with regulatory requirements, thereby enhancing the overall security posture of the organization.
- Scalability: The best RMM tools are scalable and can accommodate the growing needs of organizations as they expand their IT infrastructure or onboard new clients. Also take into account if they work for all operating systems in your organizations. For example, you may need Mac RMM tools.

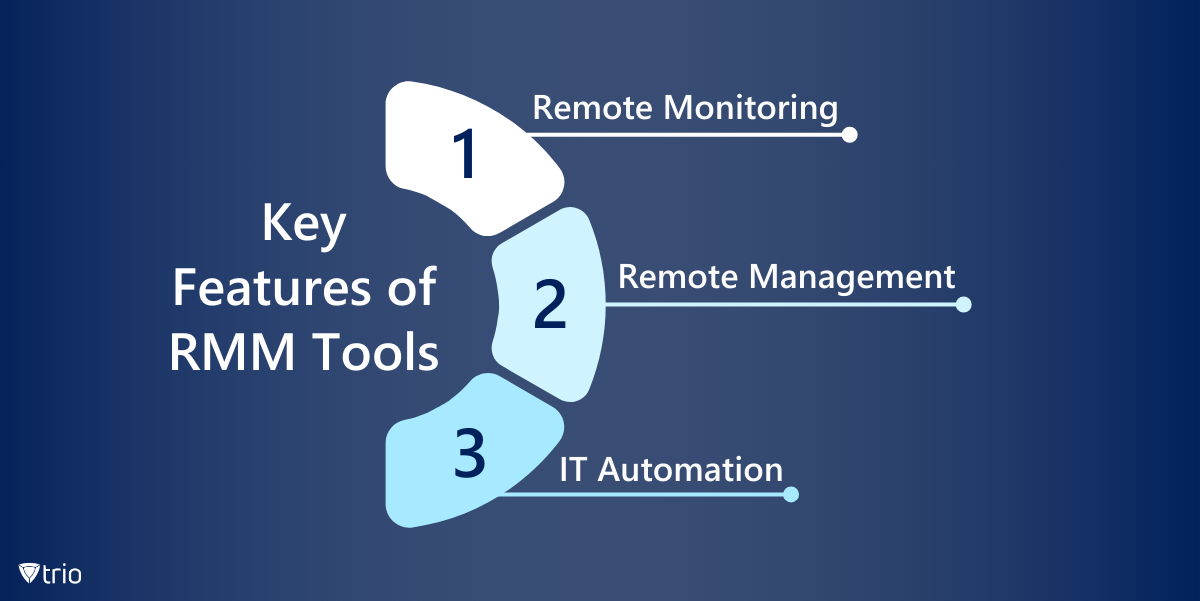
Key Features of RMM Tools
Remote Monitoring and Management tools are used by IT service providers and managed service providers (MSPs) to remotely monitor and manage clients' IT infrastructure, systems, and endpoints. These tools typically offer a range of functionalities, including:
- Remote Monitoring: Constantly monitoring the health and performance of servers, workstations, networks, and other IT assets in real-time. This includes tracking metrics such as CPU usage, disk space, memory usage, network bandwidth, etc.
- Remote Management: Allowing administrators to remotely troubleshoot issues, perform maintenance tasks, and deploy software updates or patches across multiple devices without the need for physical presence.
- IT Automation: Automating routine tasks and processes to improve efficiency and reduce manual workload. This can include tasks like software deployment, patch management, system backups, and more.
Choosing the Right RMM Tools for Effective IT Infrastructure Management
Choosing the right Remote Monitoring and Management (RMM) tool is crucial for effectively managing and supporting your organization's IT infrastructure or your clients' environments if you're a managed service provider (MSP). Here's a structured approach to help you select the best RMM tool for your needs:
- Define Your Requirements: Start by clearly defining your organization's or clients' requirements. Identify the specific functionalities and features you need from an RMM tool. Consider factors such as remote monitoring, management capabilities, security features, automation, scalability, and integration with other tools or systems.
- Evaluate Your Budget: Determine your budget for RMM tools, including upfront costs, ongoing subscription fees, and any additional expenses such as training and implementation. Consider the value provided by each option relative to its cost.
- Assess Scalability: Consider the scalability of the RMM tool to accommodate your organization's growth or the expansion of your client base. Ensure that the tool can handle the increasing demands of your IT infrastructure or client requirements without significant performance degradation or additional costs.
- Request Demos and Trials: Contact the vendors of the shortlisted RMM tools to request product demonstrations and trial access. Take advantage of demos to see the tools in action and assess their usability, interface, and feature set. Test the trial versions to evaluate performance, reliability, and compatibility with your environment.
- Consider Integration: Evaluate how well each RMM tool integrates with your existing IT infrastructure, systems, and third-party applications. Choose a tool that seamlessly integrates with your preferred tools and platforms to avoid compatibility issues and streamline workflows.
- Assess Support and Training: Consider the level of support and training provided by the RMM vendor. Evaluate the availability of technical support, documentation, training resources, and user communities. Ensure that you have access to the assistance you need to deploy, configure, and use the RMM tool effectively. For example, many open-source RMM tools don’t come with support and training.
- Review Security Features: Pay close attention to the security features offered by each remote monitoring software, especially if you're managing sensitive data or serving clients with strict security requirements. Look for features such as encryption, role-based access control, audit logs, and compliance management capabilities.
- Seek Feedback: Gather feedback from stakeholders within your organization or from clients if you're an MSP. Solicit input from IT administrators, technicians, and end-users who will interact with the RMM tool on a regular basis. Consider their preferences, concerns, and experiences to make an informed decision.

RMM and MDM Solutions Go Hand in Hand
RMM tools excel in monitoring and managing traditional IT infrastructure components such as servers, workstations, and network devices, providing real-time insights into system health and performance. On the other hand, MDM (Mobile Device Management) solutions, such as Trio, specialize in managing and securing mobile devices like smartphones and tablets, enforcing security policies, and controlling access to corporate resources. Together, these tools enable IT administrators to oversee and manage a diverse range of endpoints from a unified console, streamlining administrative tasks and improving operational efficiency.
The integration of RMM and MDM solutions ensures consistency in security practices and policy enforcement across all endpoints, whether traditional IT infrastructure or mobile devices. By enforcing uniform security policies and configurations, organizations can mitigate security risks and maintain compliance with regulatory requirements. Furthermore, the combination of remote support and troubleshooting capabilities offered by both RMM and MDM tools enables IT teams to quickly diagnose and resolve issues on all managed endpoints, minimizing downtime and maximizing productivity. This integrated approach to endpoint management enhances visibility, control, and security across the entire IT environment, facilitating proactive monitoring, efficient management, and streamlined operations.
Conclusion
In conclusion, the integration of RMM and MDM solutions emerges as a formidable alliance in the realm of endpoint management, offering organizations a comprehensive and cohesive approach to overseeing their digital ecosystems. By harnessing the combined power of RMM and MDM tools, IT teams can ensure uniform security practices, streamline administrative tasks, and bolster operational efficiency across all endpoints, from traditional IT infrastructure components to mobile devices.
This integrated approach not only enhances visibility and control but also fortifies the security posture of organizations, enabling them to navigate the complexities of modern IT environments with confidence and agility. As organizations continue to grapple with evolving technological landscapes, the synergy between RMM and MDM tools stands as a beacon of efficiency and effectiveness in the pursuit of optimal endpoint management. If you’re looking for a simple and scalable MDM solution for your organization, we recommend you try out Trio’s free demo.
Get Ahead of the Curve
Every organization today needs a solution to automate time-consuming tasks and strengthen security.
Without the right tools, manual processes drain resources and leave gaps in protection. Trio MDM is designed to solve this problem, automating key tasks, boosting security, and ensuring compliance with ease.
Don't let inefficiencies hold you back. Learn how Trio MDM can revolutionize your IT operations or request a free trial today!





