In the ever-evolving landscape of digital identity management, organizations are constantly seeking efficient and secure solutions to streamline user provisioning, access control, and compliance. One such solution that has gained prominence in recent years is SCIM, or System for Cross-domain Identity Management. SCIM offers a standardized protocol for automating the management of user identities across disparate systems and platforms, providing a centralized approach to identity management that enhances efficiency, security, and scalability. In this blog post, we delve into the benefits of integrating SCIM with Mobile Device Management (MDM) solutions, exploring how this combination empowers organizations to effectively manage user identities in today’s dynamic IT environments.
SCIM Definition
SCIM stands for System for Cross-domain Identity Management. It’s an open standard protocol that enables the automation of user provisioning and management in cloud-based applications and services. SCIM provides a standardized way for identity providers (such as an organization’s directory service) to manage user identities and access privileges across different systems and services, including those hosted on-premises and in the cloud. This helps streamline user lifecycle management processes and ensures consistency and security across multiple platforms and applications.
Using System for Cross-domain Identity Management offers several advantages. SCIM provides a standardized way to manage user identities and access across different systems and platforms. It enables automated user provisioning, deprovisioning, and synchronization processes. This automation reduces manual intervention, minimizes errors, and ensures that user accounts and access rights are promptly updated across all connected systems, improving efficiency and security.
SCIM is designed to support scalability, making it suitable for organizations of all sizes. Whether managing a few dozen users or thousands of users across multiple systems and services, SCIM can efficiently handle the complexities of user lifecycle management. SCIM also helps enhance security by ensuring that access rights are promptly granted or revoked as users join, move within, or leave the organization. This reduces the risk of unauthorized access and helps organizations maintain compliance with regulatory requirements.

How Do You Integrate With SCIM?
Integrating with SCIM involves several steps:
- Implement SCIM Protocol: Ensure that your system or application supports the SCIM protocol. This typically involves implementing SCIM endpoints for user provisioning, updating, and deprovisioning.
- Configure SCIM Endpoints: Configure your SCIM endpoints to allow communication with external identity providers or other systems. This includes setting up endpoints for user provisioning, updating, and deprovisioning.
- Define Schema Mapping: Map the attributes of your system or application to the SCIM schema. This ensures that user data can be properly synchronized between systems using SCIM.
- Authenticate and Authorize Requests: Implement SCIM authentication and multi-factor authorization mechanisms to ensure that only authorized users or systems can access your SCIM endpoints. This may involve using OAuth tokens, API keys, or other authentication methods.
- Handle SCIM Requests: Implement logic to handle SCIM requests received from external identity providers or systems. This includes processing requests for user provisioning, updating user attributes, and deprovisioning users.
- Handle Errors and Exceptions: Implement error handling logic to handle cases where SCIM requests fail or encounter errors. This may involve returning appropriate HTTP status codes and error messages to the requesting system.
- Test Integration: Thoroughly test your SCIM integration to ensure that user provisioning, updating, and deprovisioning functions as expected. This includes testing various scenarios such as creating new users, updating user attributes, and deprovisioning users.
- Monitor and Maintain Integration: Once your SCIM integration is in place, monitor its performance and reliability to ensure that it continues to function as expected. Make any necessary updates or improvements to address any issues that arise over time.

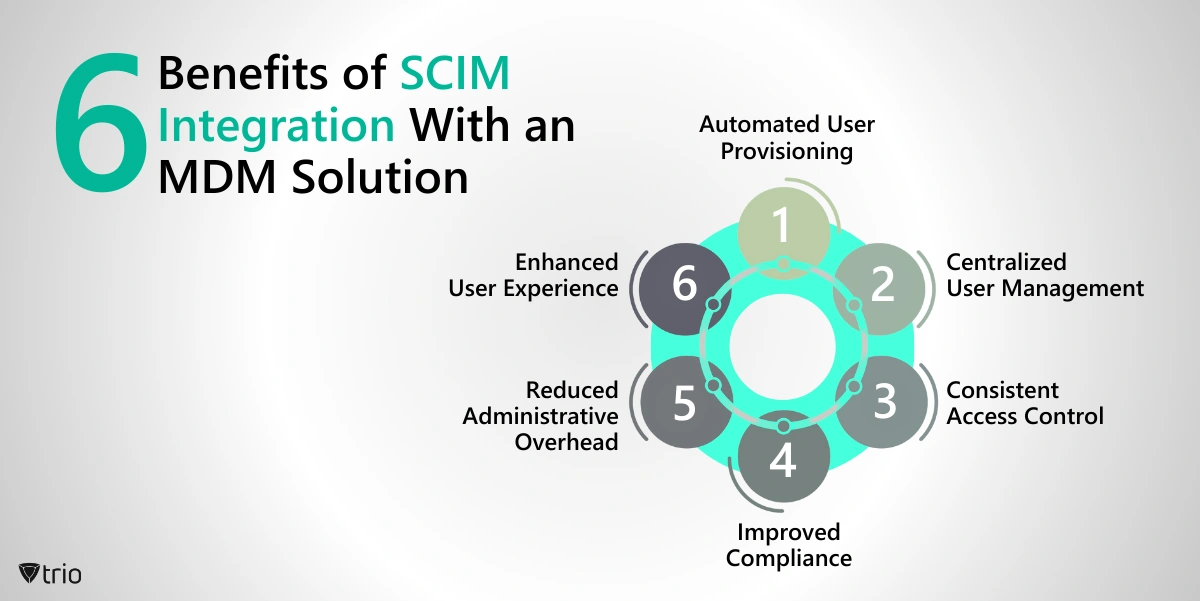
Benefits of SCIM Integration With an MDM Solution
Integrating SCIM with Mobile Device Management solutions offers several benefits.
-
Automated User Provisioning
SCIM integration automates the provisioning of user accounts and access rights within the MDM solution. When new users are added or updated in the identity provider system, SCIM facilitates the automatic synchronization of this information with the MDM, ensuring users have appropriate access to mobile devices and resources.
-
Centralized User Management
SCIM enables centralized user management across various systems and platforms. With SCIM integrated into the MDM solution, administrators can manage user identities, access permissions, and group memberships from a single location, improving efficiency and reducing the risk of errors associated with manual processes.
-
Consistent Access Control
By leveraging SCIM, organizations can enforce consistent access control policies across all connected systems and applications, including mobile devices managed by the MDM solution. This helps enhance security by ensuring that users only have access to the resources they need, based on their roles and permissions.
-
Improved Compliance
SCIM integration with MDM solutions helps organizations maintain compliance with regulatory requirements and internal security policies. Automated user provisioning and de-provisioning processes ensure that access rights are promptly granted or revoked as users join, move within, or leave the organization, reducing the risk of unauthorized access.
-
Reduced Administrative Overhead
Automating user lifecycle management tasks through SCIM integration with MDM solutions reduces the administrative burden on IT staff. This frees up time and resources that can be allocated to other strategic initiatives, improving overall productivity and efficiency.
-
Enhanced User Experience
Seamless integration between SCIM and MDM solutions ensures a smoother user experience. Users can quickly and easily access mobile devices and corporate resources without encountering delays or disruptions caused by manual account provisioning or synchronization issues.
Conclusion
In conclusion, the integration of SCIM with Mobile Device Management (MDM) solutions represents a significant advancement in the realm of identity management. By leveraging SCIM’s standardized protocol for cross-domain identity management, organizations can automate user provisioning, ensure consistent access control, and enhance security across various systems and platforms. This integration not only streamlines administrative tasks but also strengthens compliance efforts and improves the overall user experience. As organizations continue to embrace cloud technologies and mobile devices, the adoption of SCIM becomes increasingly essential for maintaining a secure and efficient IT environment. Embracing SCIM within MDM solutions heralds a new era of identity management, where simplicity, scalability, and security converge to meet the evolving needs of modern businesses.
See Trio in Action: Get Your Free Trial Now!
We recommend you use Trio as your MDM solution of choice. Trio utilizes the SCIM protocol, which establishes a standard set of REST APIs to automate creating and managing user accounts and access permissions across multiple systems and applications. Through integration with SCIM-supported systems, Trio ensures that user access remains consistently up-to-date and accurate. Try out Trio’s free demo today!
Get Ahead of the Curve
Every organization today needs a solution to automate time-consuming tasks and strengthen security.
Without the right tools, manual processes drain resources and leave gaps in protection. Trio MDM is designed to solve this problem, automating key tasks, boosting security, and ensuring compliance with ease.
Don't let inefficiencies hold you back. Learn how Trio MDM can revolutionize your IT operations or request a free trial today!




