In today’s digital age, where data breaches and cyber threats loom large, ensuring the security and integrity of sensitive information is paramount for organizations across all industries. One crucial framework that has emerged to address these concerns is SOC 2 compliance. Developed by the American Institute of CPAs (AICPA), SOC 2 sets stringent standards for managing and securing data stored in the cloud, particularly for service providers handling customer data. In this comprehensive guide, we delve into everything organizations need to know about SOC 2 compliance.
What Is SOC 2 Compliance?
SOC 2 stands for Service Organization Control 2. The SOC 2 compliance is a framework developed by the American Institute of CPAs (AICPA) that sets standards for managing and securing sensitive data stored in the cloud. It’s specifically designed for service providers like SaaS companies, data centers, and managed service providers who store customer data in the cloud. SOC 2 compliance focuses on five trust principles: security, availability, processing integrity, confidentiality, and privacy. These SOC 2 principles ensure that organizations have the necessary controls and processes in place to protect customer data and ensure the reliability and security of their systems. Types of compliance best practices are essential for ensuring that organizations adhere to SOC 2 standards and effectively manage and secure sensitive data stored in the cloud.
Companies undergo a SOC 2 audit conducted by an independent third-party auditor to assess their compliance with these criteria and implement compliance training best practices. Upon successful completion of the audit, the organization receives a SOC 2 certification, which they can share with their customers to demonstrate their commitment to data security and compliance.

Why Is SOC 2 Compliance Important?
Complying with the SOC 2 compliance checklist and ensuring adherence to Compliance Settings is essential for protecting sensitive data, building trust with customers, meeting regulatory requirements, managing risks, and gaining a competitive advantage in the market. SOC 2 compliance is important for several reasons:
- Data Security: SOC 2 compliance ensures that service providers have implemented strong controls to protect sensitive data from unauthorized access, disclosure, and misuse. This is crucial in today’s digital landscape where data breaches are increasingly common.
- Customer Trust: Compliance with SOC 2 standards demonstrates to customers that a service provider takes data security and privacy seriously. It provides assurance that their data will be handled in a secure and reliable manner, which helps to build trust and confidence in the service.
- Legal and Regulatory Compliance: Many industries are subject to regulatory requirements regarding the protection of sensitive data, such as healthcare (HIPAA), finance (GLBA), and the payment card industry (PCI DSS). SOC 2 compliance helps organizations meet these regulatory obligations by providing a framework for implementing appropriate security controls. SOC 2 is among the most important IT compliances organizations should be aware of.
- Risk Management: Implementing SOC 2 controls helps organizations in identity and assessment management. This in turn mitigates risks related to data security and privacy. By adhering to SOC 2 standards, companies can better protect themselves from potential security incidents and the associated financial and reputational damages.
- Competitive Advantage: In today’s competitive business environment, having SOC 2 compliance can be a differentiator. It demonstrates a commitment to security and compliance, which can give service providers a competitive edge when attracting customers, especially those who prioritize data security and privacy.

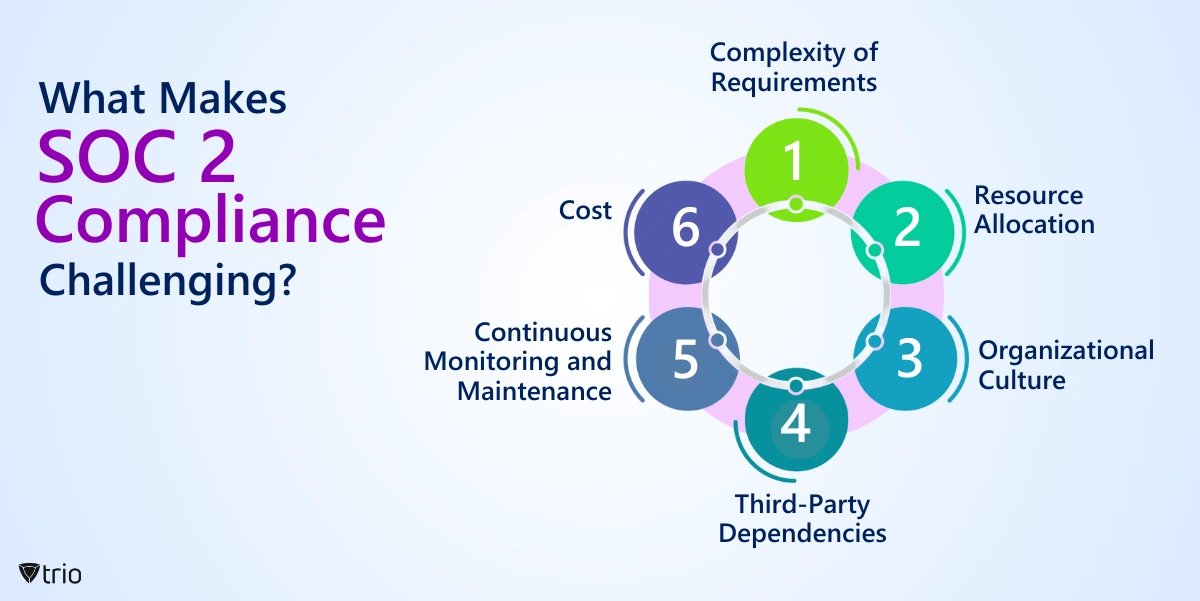
What Makes SOC 2 Compliance Challenging?
Achieving SOC 2 standards can present several challenges for organizations:
- Complexity of Requirements: SOC 2 compliance involves adherence to a comprehensive set of requirements across multiple trust service criteria (security, availability, processing integrity, confidentiality, and privacy). Understanding and implementing these requirements can be complex and time-consuming, especially for organizations with limited resources or expertise in information security.
- Resource Allocation: Achieving SOC 2 compliance requires significant time, effort, and resources. Organizations need to allocate resources for activities such as implementing security controls, conducting risk assessments, documenting policies and procedures, and undergoing audits by independent third-party auditors. This can strain internal resources and budget.
- Organizational Culture: Achieving compliance often requires a cultural shift within an organization to prioritize security and compliance. This may involve changing processes, workflows, and employee behaviors to ensure that security controls are consistently followed and maintained.
- Third-Party Dependencies: Many organizations rely on third-party vendors and service providers to deliver their products or services. Ensuring that these third parties also adhere to SOC 2 standards can be challenging, as it requires evaluating their security practices, conducting due diligence, and monitoring their compliance over time.
- Continuous Monitoring and Maintenance: Achieving SOC 2 compliance is not a one-time effort; it requires ongoing monitoring and maintenance to ensure that security controls remain effective and compliant with evolving threats and regulatory requirements. This involves regular assessments, audits, and updates to policies, procedures, and technology infrastructure.
- Cost: Achieving and maintaining SOC 2 compliance can be costly, especially for small and medium-sized organizations with limited budgets. Costs may include hiring external consultants, investing in security technologies, conducting audits, and dedicating internal resources to compliance activities.
How Is SOC 2 Compliance Relevant to MDM Solutions?
SOC 2 compliance is relevant to Mobile Device Management (MDM) solutions in several ways:
-
Data Security
MDM solutions are responsible for managing and securing mobile devices, including smartphones, tablets, and laptops, that access sensitive corporate data. SOC 2 compliance ensures that these solutions have implemented robust security controls to protect this data from unauthorized access, disclosure, and misuse.
-
Availability
MDM solutions play a critical role in ensuring the availability of corporate data and applications on mobile devices. SOC 2 compliance requires MDM providers to demonstrate the availability of their services and infrastructure to meet customer needs and expectations.
-
Processing Integrity
MDM solutions must ensure the integrity of data processing activities, such as device provisioning, configuration, and monitoring. SOC 2 compliance ensures that these processes are performed accurately, reliably, and securely to prevent data manipulation or unauthorized changes.
-
Confidentiality
MDM solutions handle sensitive corporate information stored on mobile devices, such as emails, documents, and business applications. SOC 2 compliance requires these solutions to implement controls to maintain the confidentiality of this data and prevent unauthorized access or disclosure.
-
Privacy
MDM solutions often collect and process personal information about device users, such as contact details, location data, and usage patterns. SOC 2 compliance mandates that these solutions have measures in place to protect the privacy rights of individuals and comply with applicable privacy regulations, such as GDPR or CCPA.
-
Vendor Risk Management
Organizations that use MDM solutions need assurance that their vendors adhere to strict security and compliance standards. SOC 2 compliance provides a framework for evaluating and managing the risks associated with MDM providers, ensuring that they meet the necessary security and privacy requirements.
Conclusion
In conclusion, SOC 2 compliance stands as a cornerstone in today’s digital landscape, offering a robust framework for organizations to safeguard sensitive data, build trust with customers, meet regulatory obligations, manage risks effectively, and gain a competitive edge in the market. While achieving SOC 2 compliance poses significant challenges, from the complexity of requirements to resource allocation and continuous monitoring, the benefits far outweigh the costs. Moreover, the relevance of SOC 2 compliance extends beyond traditional IT infrastructure to encompass emerging technologies like MDM solutions, where data security, availability, processing integrity, confidentiality, privacy, and vendor risk management are paramount. Incorporating compliance automation can further streamline the SOC 2 compliance process, enabling organizations to achieve and maintain compliance more efficiently and effectively.
An MDM solution that can guarantee your organization’s compliance with SOC 2 and other important IT compliance is Trio. Trio is capable of helping you comply with the following protocols:
- SSO (Single Sign-On)
- SCIM (System for Cross-domain Identity Management)
- GDPR (General Data Protection Regulation)
- SOC2 (Service Organization Control 2)
- CIS (Center for Internet Security)
- EDR (Endpoint Detection and Response)
- VPN (ZTNA)
- VPP (Volume Purchase Program)
- APNs Certificate (Apple Push Notification service)
- ADE (DEP) (Automated Enrollment Program)
- NIST (National Institute of Standards and Technology)
We recommend you try out Trio’s free demo today and see how compliance with universal standards has never been easier. By embracing SOC 2 compliance and integrating its principles into their operations, organizations can navigate the complexities of the digital age with confidence, knowing that they are equipped to protect their most valuable asset – their data.








