In the dynamic world of IT management, access provisioning is a critical task that determines how new employees integrate into a company’s digital ecosystem. For IT administrators, business owners, and IT specialists, understanding and implementing efficient access provisioning systems is essential for maintaining security and productivity. This blog post will define user provisioning, explore the most efficient methods for user access provisioning, and introduce the benefits of MDM solutions in provisioning.
User Provisioning Meaning: “What Is User Provisioning?”
User provisioning, often referred to as account provisioning, involves the creation, management, and deactivation of user accounts. This includes granting appropriate data and application access rights to users within an organization. It is a crucial part of identity management and ensures that each user has the access necessary to perform their job, while also safeguarding sensitive information.
Types of Provisioning
- Manual Provisioning: An administrator creates accounts and assigns rights individually.
- Automated User Provisioning: Systems automatically manage access rights based on predefined policies.
- Self-Service Provisioning: Users request access themselves, which is then approved or denied by administrators.
Benefits of Access Provisioning
Access provisioning offers several advantages:
- Security: Ensures only authorized personnel have access to sensitive information.
- Compliance: Helps in adhering to regulatory standards by controlling who has access to what data.
- Efficiency: Reduces the time it takes to onboard new employees, allowing them to be productive sooner.
- Scalability: Simplifies the management of user rights as a company grows.
The Process of Provisioning and Deprovisioning
Provisioning and de-provisioning are critical components of identity and access management (IAM) within any organization. Implementing these processes effectively is essential for maintaining security and operational efficiency. Let’s delve deeper into each of these processes.
Provisioning: Setting the Stage for New Employees
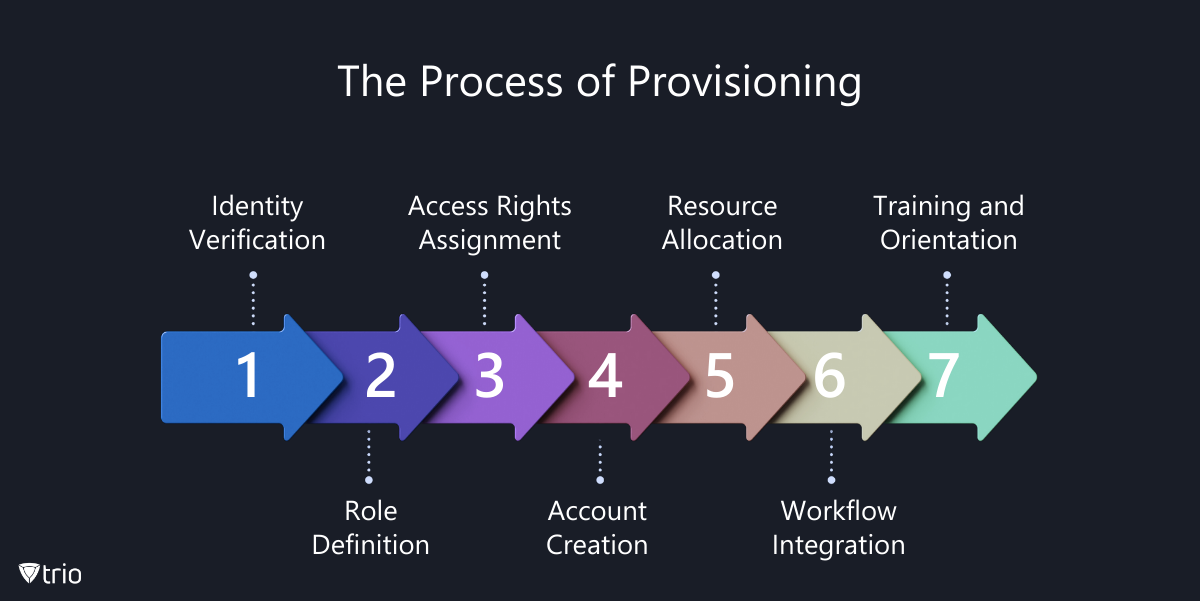
The provisioning process begins when a new employee joins an organization. It involves several key steps:
- Identity Verification: Confirming the identity of the new user to ensure that access is granted to the correct individual.
- Role Definition: Assigning a role to the new employee, which determines the level of access and the resources that they require to fulfill their job responsibilities.
- Access Rights Assignment: Based on the role, specific access rights are granted. This could include access to email accounts, databases, applications, and network resources.
- Account Creation: Creating a user account within the organization’s network and systems, which may involve setting up an email address, a directory profile, and credentials.
- Resource Allocation: Providing the necessary tools and resources, such as hardware (computers, phones) and software licenses.
- Workflow Integration: Integrating the new user into existing workflows and collaboration tools, ensuring they can participate in team activities.
- Training and Orientation: Educating the new employee on how to use the resources provided, including security protocols and best practices.
Automated tools and user provisioning software can streamline these steps, ensuring that they are carried out consistently and efficiently.
Deprovisioning: Safeguarding Data When Employees Leave
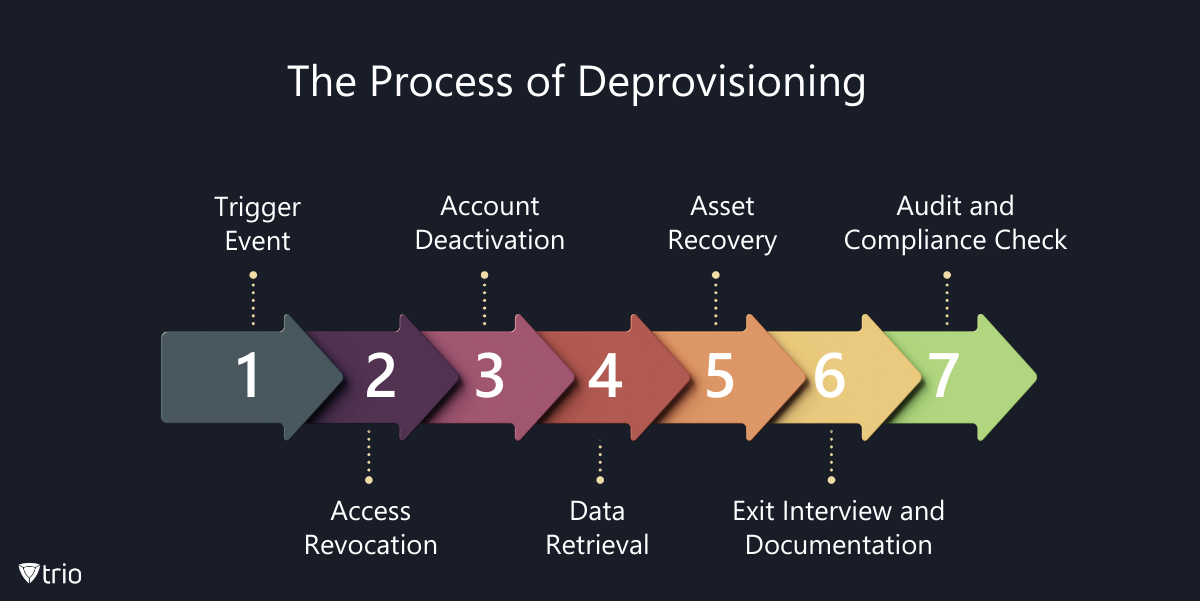
Deprovisioning is equally important as provisioning, yet it is often overlooked. It is the process of revoking access and recovering resources when an employee leaves the company or changes roles. The steps include:
- Trigger Event: This could be a resignation, termination, or role change that initiates the de-provisioning process.
- Access Revocation: All access rights associated with the user are revoked to prevent unauthorized access to sensitive information.
- Account Deactivation: The user’s account is either disabled or completely removed from all systems and applications.
- Data Retrieval: Any work-related data or documents owned by the user are transferred to a designated person or archived according to company policy.
- Asset Recovery: Company-owned hardware and any other physical assets are returned.
- Exit Interview and Documentation: An exit interview may be conducted to understand the reasons for departure and to document the de-provisioning process.
- Audit and Compliance Check: Ensuring that all steps were followed correctly and that the de-provisioning is documented for compliance purposes.
Efficient de-provisioning is crucial for preventing potential security breaches and ensuring that only current employees have access to company resources.
Most Efficient Access Assignment and Management: Automated User Provisioning
The most efficient way to assign and manage access rights for new employees is through automated user provisioning. This method uses software to provision access based on predefined policies, roles, and workflows. Automation reduces the risk of human error, ensures consistent access control, and saves significant time for IT departments. Here is how automated user provisioning brings on the results:
Consistency: Automation ensures that every user’s access rights are provisioned according to the same set of predefined rules and policies, which minimizes the risk of discrepancies.
Efficiency: Manual provisioning can be time-consuming and prone to errors. Automated systems can provision access in a fraction of the time, freeing up IT staff to focus on more strategic tasks.
Scalability: As organizations grow, the number of users to provision can become unmanageable for manual processes. Automated provisioning systems can easily scale to handle an increasing number of user accounts without a corresponding increase in the workload for IT staff.
Security: Automated provisioning reduces the risk of unauthorized access by ensuring that only the appropriate users have access to sensitive systems and data. It also ensures that access rights are revoked immediately when a user’s role changes or they leave the organization.
Compliance: Many industries have strict regulatory requirements regarding who can access what data and when. Automated provisioning helps organizations maintain compliance with these regulations by providing traceable and auditable records of all provisioning actions.
Reduced Human Error: The less human intervention in the process, the lower the chance of mistakes. Automation significantly reduces the risk of accidentally granting excessive permissions or forgetting to revoke access.
How MDM Solutions Can Help with Provisioning
Mobile Device Management (MDM) solutions are designed to streamline the management of mobile devices within an organization. They can also play a crucial role in user provisioning through:
- Device Enrollment
- Application Management
- Policy Enforcement
- Remote Management
- User Authentication
- Reporting and Monitoring
Introducing Trio MDM
Trio MDM is a state-of-the-art user provisioning software designed to streamline the process of access provisioning for new employees. It caters specifically to the needs of IT administrators and companies looking to enhance their security and operational efficiency.
How Trio MDM Benefits IT Administrators and Companies
Automated Provisioning: Trio MDM automates the provisioning process, reducing manual work and the potential for errors.
Role-Based Access Control (RBAC): Access rights are assigned based on predefined roles within the company, ensuring consistency and compliance.
Audit Trails and Reporting: Provides detailed logs and reports for monitoring and auditing purposes.
Integration with Other Systems: Seamlessly connects with HR systems and other applications to ensure access rights are aligned with employee status.
Addressing Challenges with Trio MDM
Trio MDM is equipped to handle various challenges that IT administrators face:
Rapid Onboarding: Quickly provision access for a large number of new employees without compromising security.
Compliance Requirements: Maintain stringent compliance standards with automated and accurate access control.
User Lifecycle Management: Manage the entire lifecycle of a user from onboarding to offboarding, ensuring no outdated access rights remain.
Emphasizing Automated User Provisioning Features
Trio MDM stands out with its advanced features in automated user provisioning:
Self-Service Portals: Empower users to request access while maintaining control through approval workflows.
Policy Enforcement: Ensure that access rights are granted according to strict company policies.
Scalable Architecture: Whether dealing with tens or thousands of users, Trio MDM scales to meet the demand.
Conclusion: The Efficient Way for User Provisioning
For IT administrators, business owners, and IT specialists, efficient access provisioning is non-negotiable. By leveraging automated user provisioning, particularly through solutions like Trio MDM, organizations can enhance security, ensure compliance, and improve overall productivity. To witness firsthand the positive impact that such a system can have on your operation, you’re invited to try out Trio’s free demo and see how you can make a difference in IT automation at your organization.
See Trio in Action: Get Your Free Trial Now!
As technology evolves, so do the solutions that enable businesses to remain agile and secure in their operations. With the right tools in place, access provisioning becomes a streamlined, efficient process that supports the growth and success of any organization.
Get Ahead of the Curve
Every organization today needs a solution to automate time-consuming tasks and strengthen security.
Without the right tools, manual processes drain resources and leave gaps in protection. Trio MDM is designed to solve this problem, automating key tasks, boosting security, and ensuring compliance with ease.
Don't let inefficiencies hold you back. Learn how Trio MDM can revolutionize your IT operations or request a free trial today!




