Endpoint Security
Verdächtige Aktivität
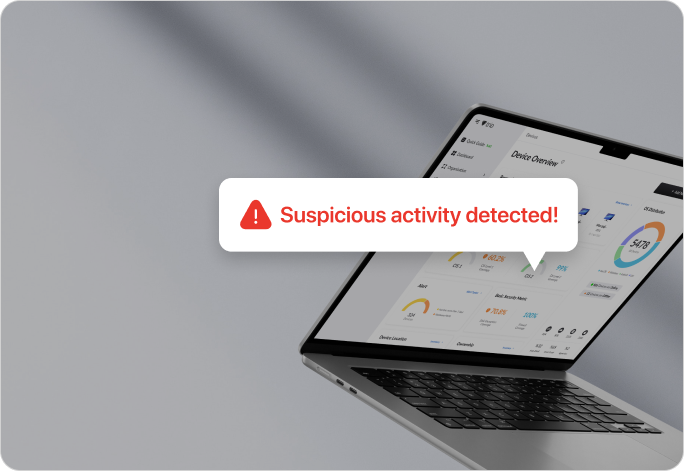
Verdächtige Aktivitäten überwachen
Schützen Sie Ihr Unternehmen vor Cyber-Bedrohungen mit dem Endpunkt-Sicherheitsmanagement von Trio. Unser fortschrittliches Überwachungssystem erkennt und analysiert verdächtige Aktivitäten in Ihrem Netzwerk und stellt sicher, dass potenzielle Bedrohungen erkannt und neutralisiert werden, bevor sie Schaden anrichten können.
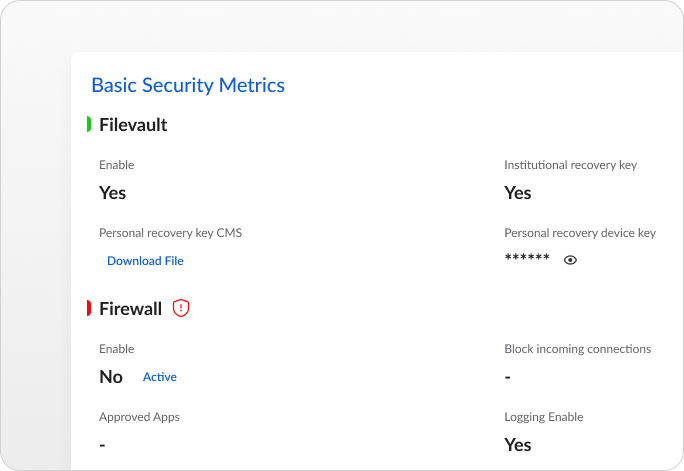
Sicherheits-Metriken
Trio Endgerätesicherheit bietet Ihnen den Komfort, den Sie brauchen, mit :
- Überwachung und Analyse der Netzwerkaktivität in Echtzeit
- Erkennung und Neutralisierung von potenziellen Bedrohungen
- Fortschrittliches Warnsystem für sofortige Reaktion auf verdächtige Aktivitäten
- Umfassende Berichterstattung über Sicherheitsvorfälle und Schwachstellen
Verstärken Sie
Ihr Unternehmen
CIS
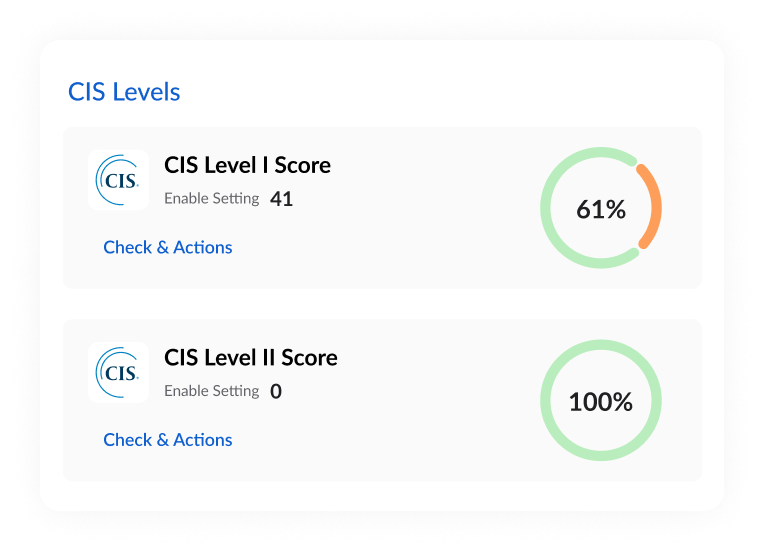
Center for Internet Security (CIS)
In the context of endpoint security, leveraging the CIS Benchmarks can assist organizations in setting up and maintaining secure configurations for their endpoint devices, reducing the risk of vulnerabilities and attacks. These benchmarks cover a wide range of technologies, operating systems, and applications, and they are regularly updated to address emerging threats and vulnerabilities.
Compliance
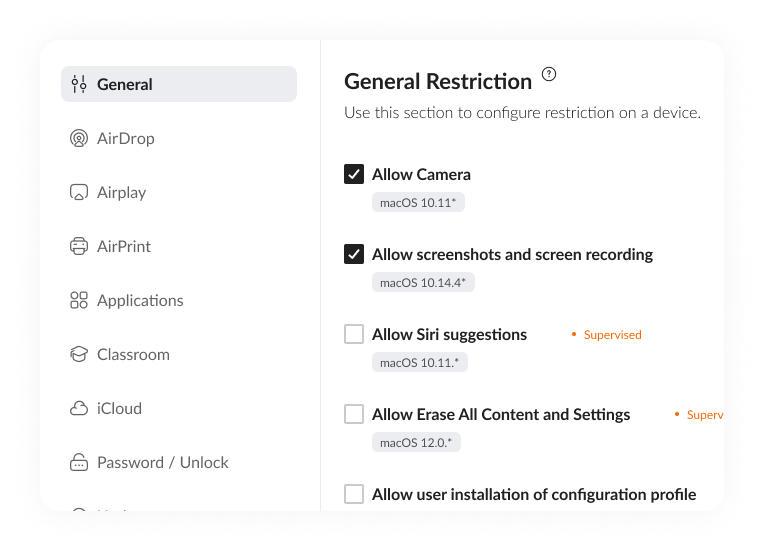
Frameworks and Regulations
Trio aligns with various compliance requirements based on industry and the type of data being processed. Examples include the General Data Protection Regulation (GDPR), Payment Card Industry Data Security Standard (PCI DSS), Health Insurance Portability and Accountability Act (HIPAA), and ISO 27001.
EDR
Endpoint Detection and Response (EDR)
Trio offers an advanced EDR solution that provides real-time visibility into endpoint activities and behaviors. Our solution gathers and analyzes extensive endpoint data, enabling organizations to promptly detect and respond to potential security threats. With our advanced analytics, machine learning, and threat intelligence capabilities, Trio can identify patterns and anomalies that may indicate malicious activity, allowing organizations to take immediate action to protect their systems and data.
Key Functionality
- Real-time monitoring of files and applications.
- Support Apple’s Endpoint Security Framework
- Remotely terminate processes
- Quarantine malicious files
- Detect suspicious activity
- Provide alerts and notifications
- Enforce custom allow/block lists
Why Your Enterprise Can't Go Without Threat Protection
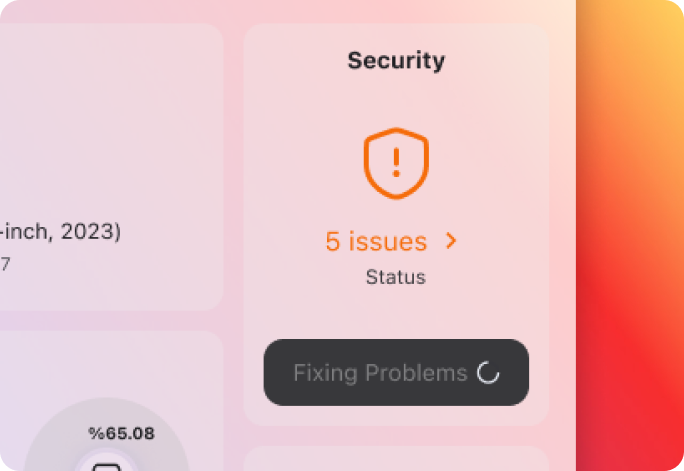
Security is Your Never-Ending Battle
Endpoint management is a crucial aspect of any comprehensive security strategy. While implementing firewalls and other network security measures are important, more is needed to protect an organization's assets fully. Endpoint devices, such as laptops, desktops, and mobile devices, are often the entry point for cyberattacks. By effectively managing and securing these endpoints, organizations can add an additional layer of protection to their network.
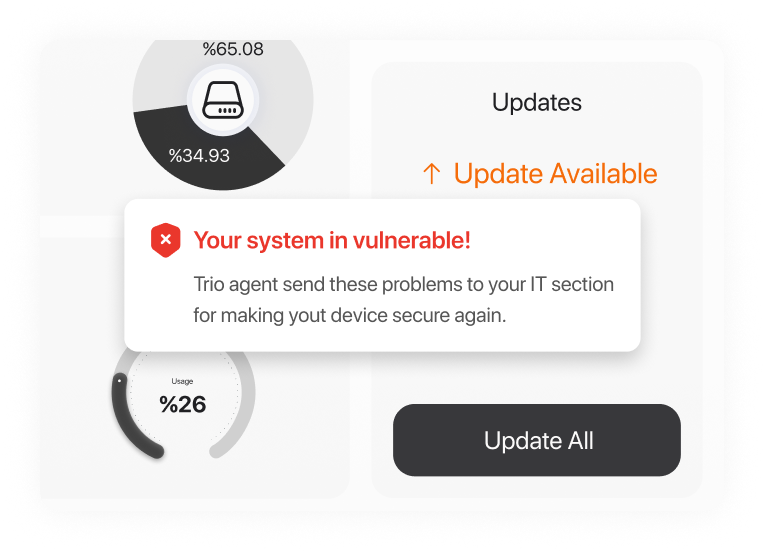
Vulnerability Management
Vulnerability management is a critical component of endpoint management and plays a crucial role in maintaining the security of your assets. Identify and address any system vulnerabilities before attackers can exploit them. This includes conducting regular vulnerability scans and assessments and prioritizing identified vulnerabilities. With Trio, ensure all endpoints are updated with the latest patches and security updates.